In encryption, the data is translated to some other unreadable form using mathematical techniques and algorithms. The encryption methodology is stored in the files known as keys which can be either managed by the system itself, or the user can manually manage them by himself. AWS provides us with four different methods of encryption for our S3 buckets.
S3 Encryption Methods
There are two main encryption methods which can be classified further as follows.
Server-Side Encryption
Server-side encryption means that the server itself manages the encryption process, and you have lesser things to manage. For S3 buckets, we need three types of server-side encryption methods based on how the encryption keys will be managed. For default encryption, we must apply one of these methods.
- Server-Side Encryption with S3 Managed Keys (SSE-S3)
This is the most simple type of encryption for S3. Here the keys are managed by S3, and for further security, these keys are themselves kept in the encrypted form. - Server-Side Encryption with AWS KMS Managed Keys (SSE-KMS)
Here the encryption keys are provided and managed by AWS key management service. This provides slightly better security and some other advances over SSE-S3. - Server-Side Encryption with Customer-Provided Keys (SSE-C)
In this method, AWS has no role in key management, the user sends the keys for each object himself, and S3 just completes the encryption process. Here the customer is responsible for keeping track of his encryption keys. Moreover, the data in flight should also be secured using HTTPs as the keys are sent with the data.
Client-Side Encryption
As the name implies, client-side encryption means that the client carries out the total encryption procedure locally. The user will upload encrypted data to the S3 bucket. This technique is mostly applied when you have some strict organizational rules or other legal requirements. As here, AWS has no role in doing anything. You will not see this option in the default encryption section of S3, and we cannot enable this as our default encryption method for Amazon S3 buckets.
Configure default Encryption on S3
In this article, we will see how to enable default encryption for your S3 buckets, and we are going to consider two ways to do this.
- Using AWS Management Console
- Using AWS Command Line Interface (CLI)
Enable S3 Encryption Using Management Console
First, we need to log into your AWS account either using the root user or any other user who has access and permission to manage the S3 buckets. You will see a search bar at the top of the management console, simply type S3 there, and you will get the results. Click on S3 to start managing your buckets using the console.
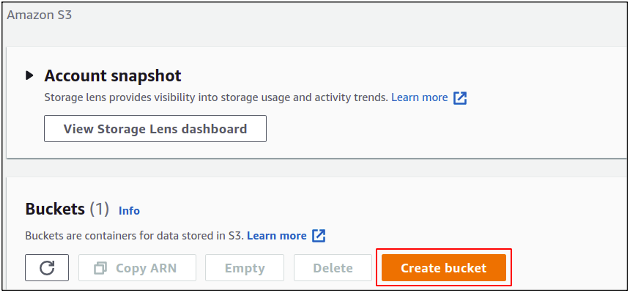
Click on create a bucket to get started with S3 bucket creation in your account.
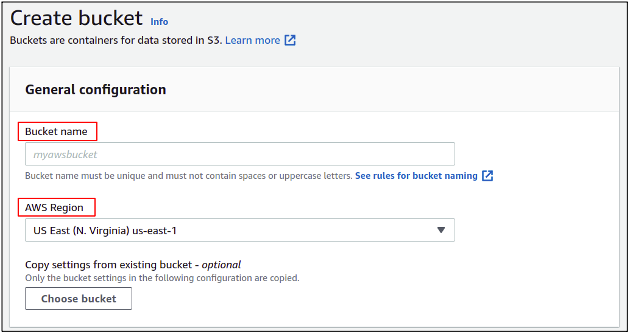
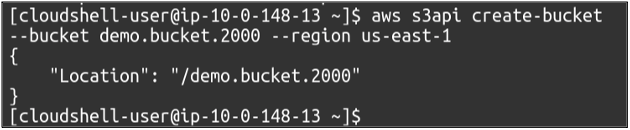
In the bucket creation section, you need to provide a bucket name. The bucket name must be unique in the whole AWS database. After that, you need to specify the AWS region where you want your S3 bucket to be placed.
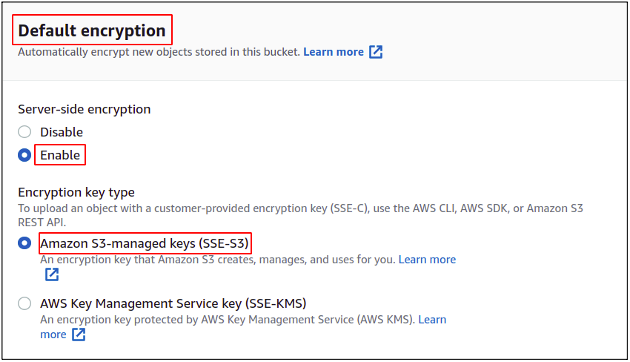
Now scroll down to the default encryption section, enable the encryption, and choose the method you want. For this example, we are going to choose SSE-S3.
Click on the create bucket in the bottom right corner to finish the bucket creation process. There are also a few other settings to manage but simply leave them as default as we have nothing to do with them for now.
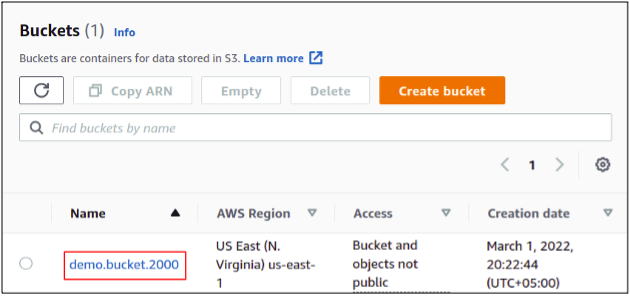
So finally, we have our S3 bucket created with default encryption enabled on it.
Let’s now upload a file to our bucket and check whether it is encrypted or not.
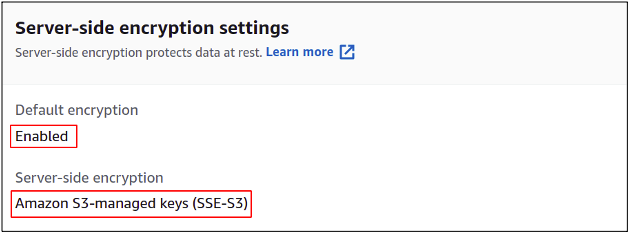
Once the object is uploaded, click over it to open the properties and drag it down to encryption settings, where you can see that encryption is enabled for this object.
So finally, we have seen how to configure S3 bucket encryption in our AWS account.
Enable S3 Encryption Using AWS Command Line Interface (CLI)
AWS also provides us the ability to manage our services and resources using the command line interface. Most professionals prefer using the command line interface as the management console has some limitations, and the environment keeps on changing while the CLI remains as it is. Once you get a firm grip over CLI, you will find it handier as compared to the management console. The AWS CLI can be set up on any environment, either Windows, Linux or Mac.
So our first step is to create the buckets in our AWS account, for which we simply need to use the following command.
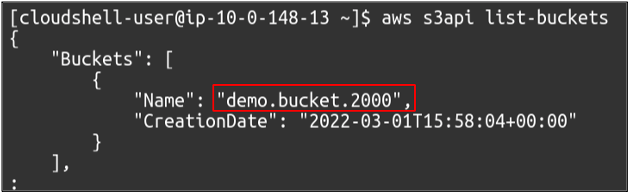
We can also view the available S3 buckets in your account using the following command.
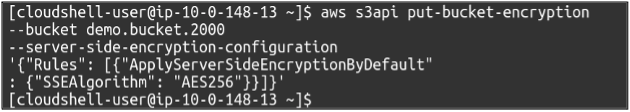
Now our bucket is created, and we need to run the following command to enable the default encryption over it. This will enable server-side encryption using S3 managed keys. The command has no output.
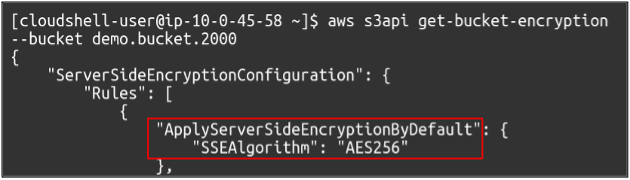
If we want to check whether the default encryption is enabled for our bucket, simply use the following command, and you will get the result in CLI.
So this means that we have successfully enabled S3 encryption and, this time, using AWS command-line interface (CLI).
Conclusion
Data encryption is very important as this may secure your important and private data on the cloud in case of any breach in the system. So Encryption provides another layer of security. In AWS, the encryption can totally be managed by S3 itself or either the user can provide and manage the encryption keys himself. With default encryption enabled, you do not have to manually enable the encryption each time when you upload the object in S3. Instead, all objects will be encrypted in the default manner unless specified otherwise.