“The sshd stands for Secure Shell Daemon. It’s a silent process that listens to all the authentication and login attempts of Linux. As soon as you start your system, the process begins.
Using sshd logs, you can monitor authorized and unauthorized login attempts on your system. This helps in keeping your system secure.
Today, we will explore how to dive into sshd logs on Ubuntu 22.04. We have presented two ways to access the sshd logs. This tutorial uses easy-to-follow Linux commands to see sshd logs. By the end of this tutorial, you will be able to explore sshd logs on your own.”
Without any further ado, let’s get started!
Guide
Following are the two ways you can check sshd logs on Ubuntu 22.04:
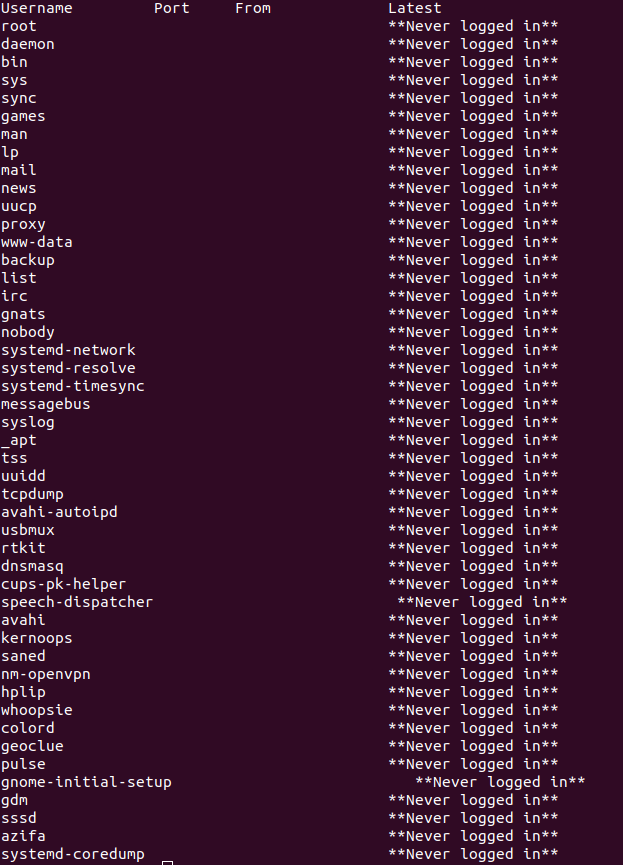
Method 1: Check SSHD Logs Using the “lastlog” Command
We make use of this method when we only want to see the login logs using sshd. To see the logs, run the lastlog command on the command line (Terminal) as shown below:
Once the command is executed, you will see all the login-related logs on your screen, as shown in the image below:
Output:
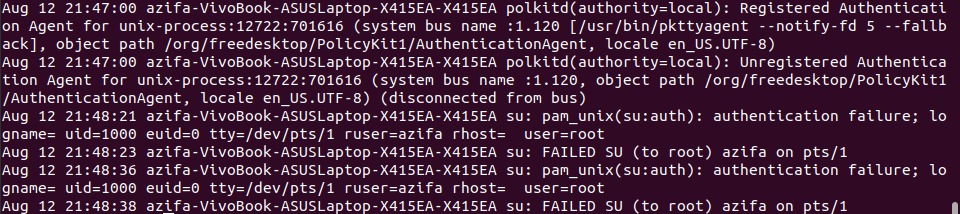
Method 2: Check SSHD Logs Using auth.log
We make use of this method when we not only want to see logs of login attempts but also all the sshd logs. To see these logs, first go to the log directory following the path /var/log. Here, there is a file with the name auth.log that keeps all the sshd logs.
To see the logs, use the cat command as shown below:
This will present to you all the sshd logs like this:
Output:
If you run into an error while accessing the auth.log file, try accessing it with root privileges. Use sudo with the cat command, and it will grant you access to the sshd logs.
Conclusion
In today’s guide, we saw in detail how to access sshd logs in Ubuntu 22.04. You saw how we could see login attempt logs using a basic Linux command. Later, we also explored how to see all the sshd logs kept in the auth.log file. Every time you try to make a new connection, share a file, or attempt to authenticate yourself, the auth.log file gets updated. Using these logs, you can monitor the security of your system to some extent by keeping an eye on the authorized and unauthorized login attempts.
We hope you liked the tutorial.