Different users access the multi-user operating system, and to monitor users’ activity, it is important to keep an eye on login history. Login history gives useful information about different users who have accessed the machine, such as username, terminal name, IP address, date, and time of logging in. Moreover, login history also helps to identify different issues, especially for troubleshooting.
This write-up is focusing on an approach to check the user login history. Before getting into that, let’s understand how Linux arrange and manage login data:
How Linux store log files?
Linux (Ubuntu) stores login data into three locations:
- var/log/utmp – It contains information about users who are currently logged in
- var/log/utmw – It contains the history of all logged-in users
- var/log/btmp – It keeps all bad login attempts
All of these files stores login information and login attempts as well.
How to check the login history?
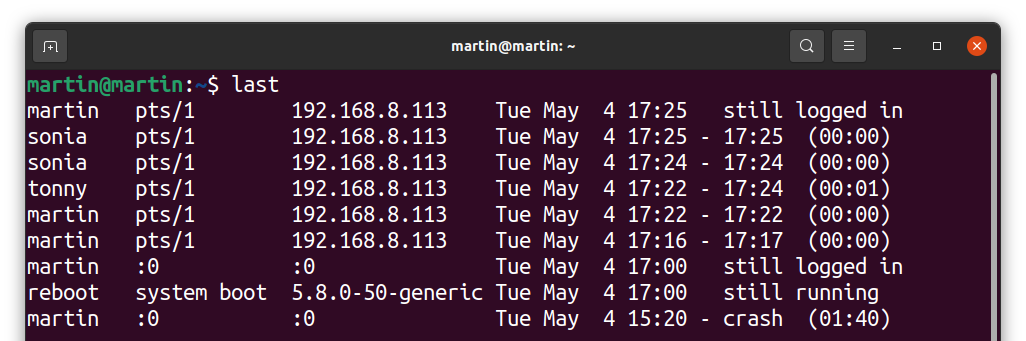
To check the login history, use the following command:
It gives information about all the users who logged in successfully. It searches through the “var/log/utmw” file and displays the history of all users who have logged in since creating the file.
The above output shows that the different users connected to the server from a machine with IP “192.168.8.113”, “pts/1” indicate that the server was accessed via SSH.
How to check the login history of a specific user?
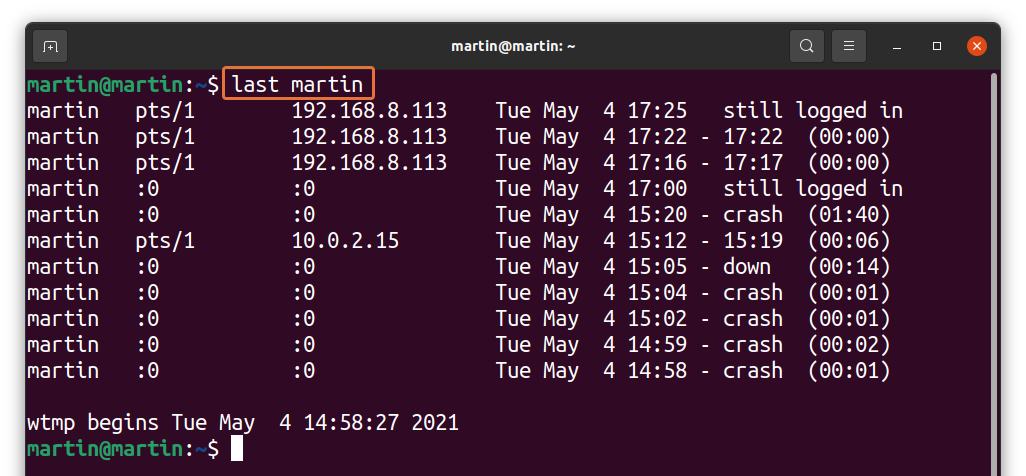
To check the login history of a specific user, uses the “last” command with the username of that particular user:
I am checking for “martin”; the command would be:
How to check the specific number of logins?
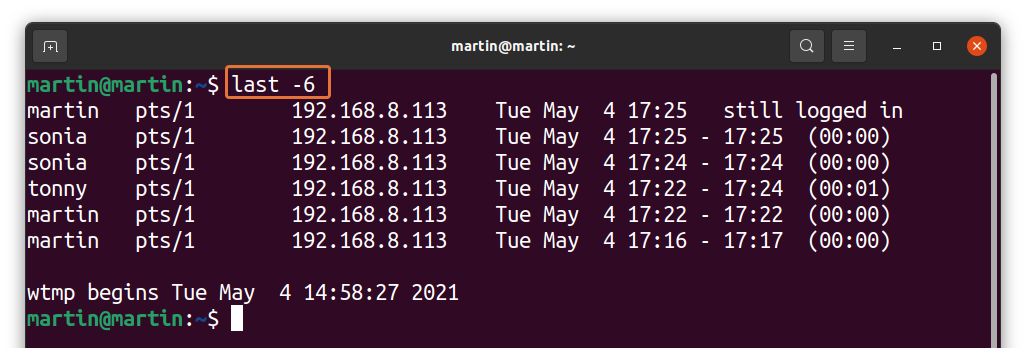
If numerous people are accessing the server, then the login history would be huge. To trim the number of logins, follow the below-mentioned syntax:
Replace “X” with the number of logins you want to display as standard output:
You can also use it with a specific username:
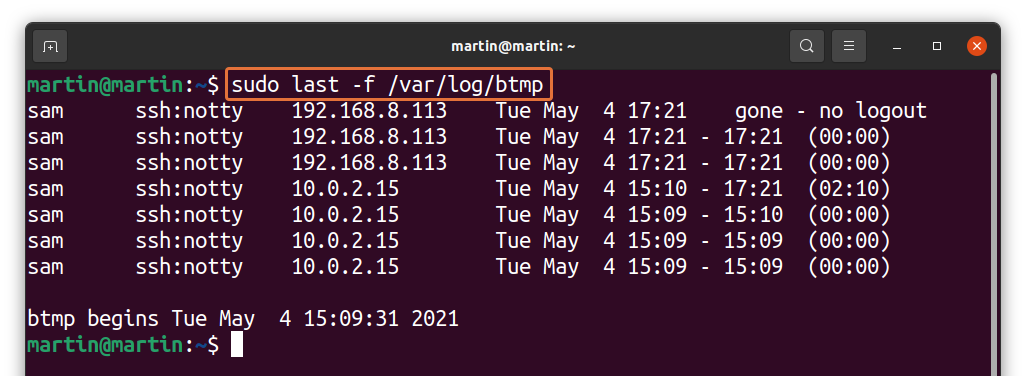
How to check bad login attempts:
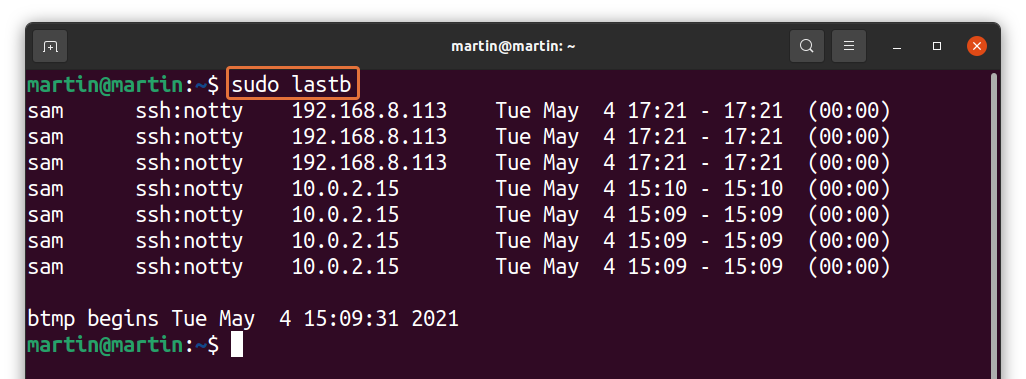
As discussed above that Linux also keeps the information of bad login attempts. To display it, use the command given below:
Or,
Observing bad login attempts is very critical for security reasons of the server. You can easily identify an unknown IP address that is probably trying to access the server.
Conclusion:
Linux is the most preferred operating system for servers in many businesses because it is a secure multi-user platform. Many users access a server, and to keep a check on user activity, we need user login information. In this guide, we learned how to examine user login history in Linux. Moreover, we also analyzed how bad attempts can be tackled to secure the server. We used the “last” command, but another tool called “aureport” tracks successful and failed logins.