Spectre Vulnerability
Spectre vulnerability breaks the isolation between the applications in your computer. So an attacker can trick a less secure application to reveal information about other secure applications from the kernel module of the operating system.
Meltdown Vulnerability
Meltdown breaks the isolation between the user, the applications and the operating system. So an attacker can write a program and it can access the memory location of that program as well as other programs and get secret information out of the system.
Spectre and Meltdown vulnerabilities are serious hardware vulnerabilities of Intel processors. In this article, I will show you how to fix Spectre and Meltdown vulnerabilities on Debian. Let’s get started.
Check for Spectre and Meltdown Vulnerabilities:
You can check for Spectre and Meltdown vulnerabilities using the Spectre and Meltdown Vulnerability Checker script.
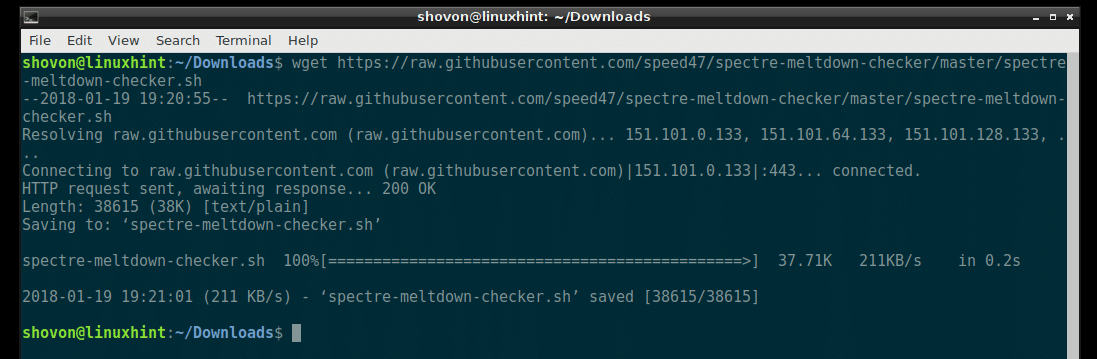
First, go to the Downloads/ directory in the user’s home directory using the following command:
Now run the following command to download the Spectre and Meltdown Checker script using wget:
spectre-meltdown-checker.sh
Spectre and Meltdown Checker script should be downloaded.
If you list the contents of the Downloads/ directory now, you should see a file spectre-meltdown-checker.sh as shown in the screenshot below.
Spectre and Meltdown Checker script needs binutils package installed on Debian to work. Before you run Spectre and Meltdown Checker script, make sure you have binutils package installed.
Run the following commands to install binutils package:
$ sudo apt-get install binutils -y
binutils should be installed.
Now run the Spectre and Meltdown Checker script with the following command:
NOTE: Run Spectre and Meltdown Checker script as root user.
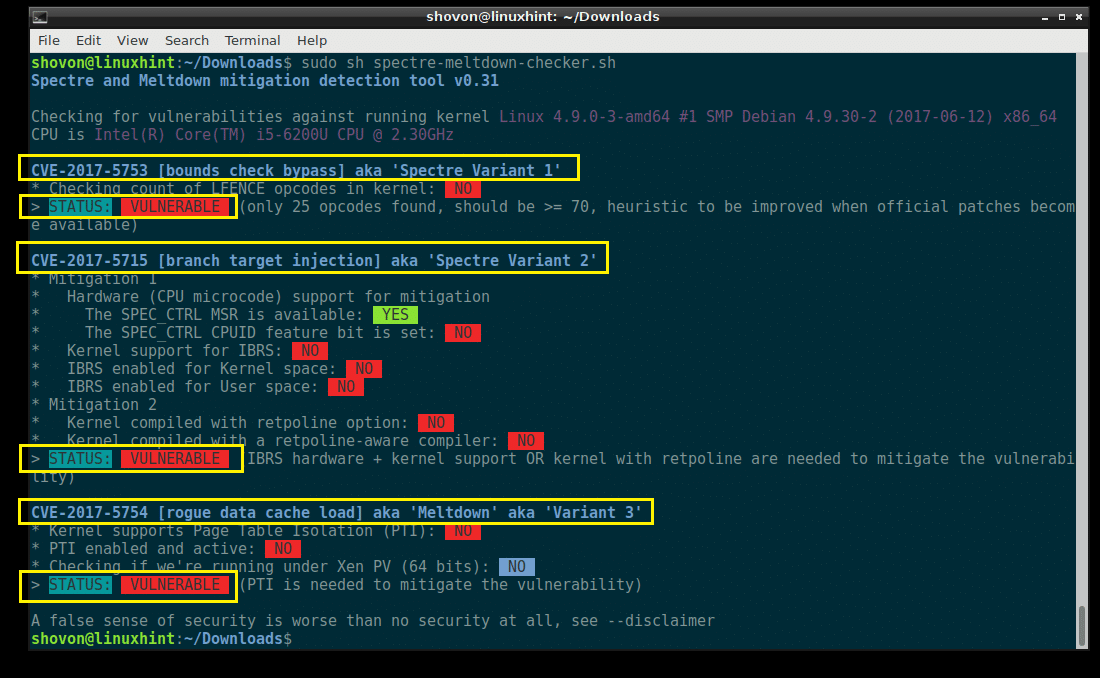
You should see something like this. This is the output of my laptop.
You can see from the screenshot below that my laptop’s processor is vulnerable to Spectre and Meltdown.
CVE-2017-5753 is the code of Spectre Variant 1, CVE-2017-5715 is the code of Spectre Variant 2, and CVE-2017-5754 is the code of Meltdown vulnerabilities. If you face any problem or if you want to learn more about them, you can search on the internet using these codes. It may help.
Patching Spectre and Meltdown Vulnerabilities:
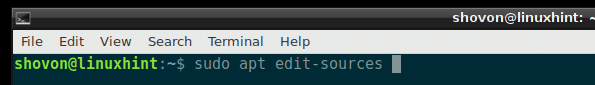
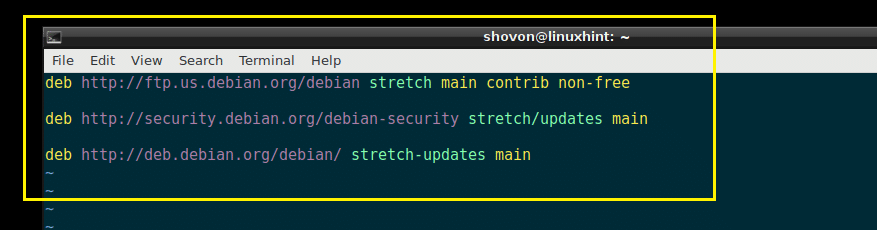
First you have to enable Debian updates and security repositories. To do that, you have to either edit /etc/apt/sources.list file directly or run the following command:
This command may ask you to select a text editor. Once you select an editor, the /etc/apt/sources.list file should be opened with the editor.
Now make sure you have stretch/updates or debian-security, and stretch-updates repository enabled as shown in the screenshot below.
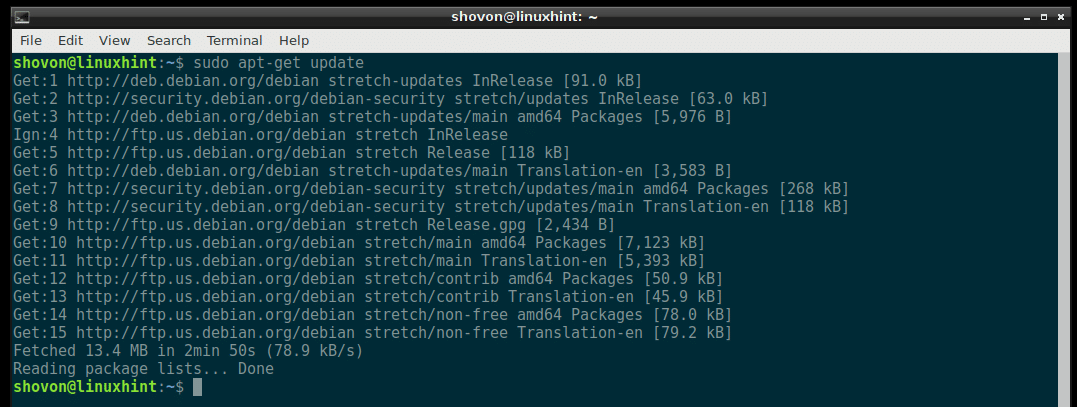
Now update the package repository cache of your Debian machine with the following command:
The package repository cache should be updated.
Before updating the kernel, make sure you check the kernel version you’re using currently with the following command. That way you can check whether the kernel is updated or not later.
As you can see, I am running 4.9.0-3 version of kernel and the architecture is amd64. If you’re running other architecture such as i386, ppc etc, you may see something different. You also pick the version of kernel depending on the architecture. For example, I am using amd64 architecture, so I am going to install an update for amd64 architecture of the kernel.
Now install the Linux kernel package with the following command:
Remember the last section, amd64, which is the architecture. You may use bash auto completion feature to find out what is available for you and pick an appropriate one.
Now press ‘y’ and press <Enter> to continue.
The kernel should be updated.
Now restart your computer with the following command:
Once your computer boots up, run the following command to check the kernel version you’re currently using.
You can see that I am using kernel version 4.9.0-5, which is a later version than 4.9.0-3. The upgrade worked perfectly.
Now you can run the Spectre and Meltdown Checker script again to see what were fixed in the kernel update.
As you can see from the screenshot below, the Meltdown vulnerability was fixed. But the Spectre vulnerabilities were not fixed in the kernel update. But keep an eye on the kernel updates as they arrive. Debian team is working hard to fix all of these issues. It may take a while, but you will get everything fixed eventually.
That’s how you check for and patch Spectre and Meltdown vulnerabilities on Debian. Thanks for reading this article.