Spectre and Meltdown vulnerabilities are hardware vulnerabilities of your processor or CPU. Mainly they are found in Intel based processors. A lot of desktops, servers and laptops are affected by spectre and meltdown vulnerabilities. The good news is that it is really hard to crack a system with these vulnerabilities. A report says, no incident was found that verifies that spectre and meltdown vulnerabilities were used to exploit user data. But it’s still a concern these days. Let’s see what these are.
Spectre Vulnerability
Spectre vulnerability breaks the isolation between the applications installed on your computer. So an attacker can trick a less secure application to reveal information about other secure applications from the kernel module of the operating system.
Meltdown Vulnerability
Meltdown breaks the isolation between the user, the applications and the operating system. So an attacker can write a program to access the memory location of that program as well as other programs and get secret information out of the system.
In this article, I will show you how to check for and patch spectre and meltdown vulnerabilities on Arch Linux. Let’s get started.
Checking Spectre and Meltdown Vulnerabilities:
First install wget, so that you can download the Spectre and Meltdown Checker script from Github from the command line easily.
To install wget, run the following command:
Press ‘y’ and press <Enter> to continue.
wget should be installed.
Now navigate to the Downloads/ directory in your user’s home directory with the following command:
Now you can download the Spectre and Meltdown Checker script using wget with the following command:
spectre-meltdown-checker.sh
The Spectre and Meltdown Checker script should be downloaded.
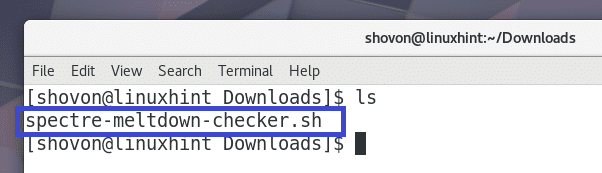
If you list the contents of the Downloads/ directory, you should see spectre-meltdown-checker.sh script file as shown in the screenshot below.
To check whether your system is vulnerable to Spectre and Meltdown, run the following command.
NOTE: You must run the script as root user.
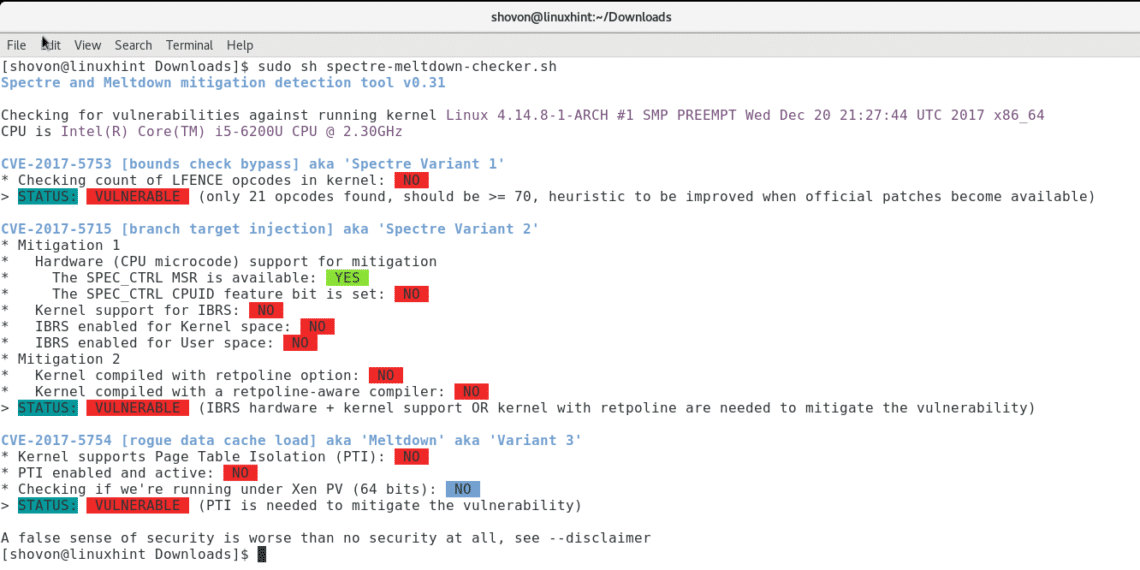
This is the output of the Spectre and Meltdown checker script on my Arch Linux computer.
You can see from the output of the Spectre and Meltdown checker script that my Arch system is vulnerable to Spectre and Meltdown. There are two variants of Spectre. CVE-2017-5753 is the code for Spectre Variant 1 and CVE-2017-5715 is the code for Spectre Variant 2. There is only one type of Meltdown vulnerability. CVE-2017-5754 is the code for Meltdown or Variant 3.
If you want to learn more about these vulnerabilities, these codes are a great way to find what you’re looking for on the internet.
Patching Spectre and Meltdown Vulnerabilities:
Patches for Spectre and Meltdown vulnerabilities come as Kernel updates. Popular Linux distributions are releasing kernel updates for patching Specture and Meltdown vulnerabilities.
Before you go through the kernel update, check the version of currently used kernel. So that you can verify whether the update worked or not.
To check the version of kernel currently used, run the following command:
You can see from the screenshot below that the current kernel version is 4.14.8-1
Now run the following command to update the kernel:
Now press ‘y’ and press <Enter> to continue.
The update process should start.
It may ask you to accept the PGP key. Press ‘y’ and press <Enter> to continue.
The kernel should be updated.
Now restart the computer with the following command:
Once your computer boots up, run the following command to check the kernel version currently used.
You can see that the kernel version is 4.14.13-1, which is more updated than 4.14.8-1
Now run the Spectre and Meltdown Checker script again with the following command:
In my computer, I got the following output as shown in the screenshot below. As you can see, Meltdown vulnerability is fixed. But Spectre Variant 1 and Spectre Variant 2 is not fixed yet. But Arch is a rolling released distribution of Linux. So you get updates as they are released. Make sure you keep an eye on the kernel updates. Everything should be fixed with time.
That’s how you check and patch Spectre and Meltdown Vulnerabilities on Arch Linux. Thanks for reading this article.