Setting up SCP and SSH:
You will need to execute the following configuration steps to perform SCP and SSH operations from localhost to remote cloud asset:
Installing AWS Systems Manager Agent on EC2 instances:
What is an SSM agent?
Amazon’s software SSM Agent can be installed and configured on an EC2 instance, virtual machine, or on-site server. SSM Agent allows the System Manager to update, control and customize these tools. The agent handles requests from the AWS Cloud System Manager service, executes them as defined in the request, and transfers the status and execution information back to the Device Manager service using the Amazon Message Delivery Service. If you track the traffic, you can see your Amazon EC2 instances and any on-site servers or Virtual Machines in your hybrid system, interacting with ec2 messages endpoints.
Installing SSM agent:
SSM Agent is installed on some EC2 and Amazon System Images (AMIs) instances by default like Amazon Linux, Amazon Linux 2, Ubuntu 16, Ubuntu 18 and 20, and Amazon 2 ECS optimized AMIs. Besides this, you can install SSM manually from any AWS region.
To install it on Amazon Linux, first of all, download the SSM agent installer and then run it using the following command :
In the above command, “region” reflects the AWS Region Identifier provided by the Systems Manager. If you cannot download it from the region, you specified, use the global URL i.e
After the installation, confirm whether the agent is running or not by the following command:
If the above command displays that the amazon-ssm-agent is stopped, then try these commands:
ubuntu@ubuntu:~$ sudo status amazon-ssm-agent
Creating IAM instance Profile:
By default, AWS Systems Manager does not have the authorization to execute actions on your instances. You must allow access by using the AWS Identity and Access Management Instant Profile (IAM). At launch, a container transfers IAM position data to an Amazon EC2 instance is called an instance profile. This condition extends to approvals on all AWS Systems Manager capability. If you are using System Manager capabilities, like the Run command, an instance profile with the basic permissions needed for Session Manager can already be attached to your instances. If your instances are already connected to an instance profile that includes the AmazonSSMManagedInstanceCore AWS Managed Policy, the appropriate Session Manager permissions are already issued. However, in specific instances, permissions may have to be changed to add session manager permissions to an instance profile. First of all, open the IAM console by logging in to the AWS management console. Now click on the “Roles” option in the navigation bar. Here choose the name of the position to be included in the policy. In the Permissions tab, choose to Add inline policy located at the bottom of the page. Click on the JSON tab and replace the already paced content with the following one:
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ssmmessages:CreateControlChannel",
"ssmmessages:CreateDataChannel",
"ssmmessages:OpenControlChannel",
"ssmmessages:OpenDataChannel"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"s3:GetEncryptionConfiguration"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"kms:Decrypt"
],
"Resource": "key-name"
}
]
}
After replacing the content, click on the Review Policy. On this page, enter the name of the inline policy like SessionManagerPermissions under the Name option. After doing this, choose the Create Policy option.
Updating Command Line Interface:
To download version 2 of AWS CLI from the Linux command line, firstly download the installation file using the curl command:
Unzip the installer using this command:
To ensure that the upgrade is enabled at the same place as the already installed AWS CLI version 2, find the existing symlink, using the which command, and the installation directory using ls command like this:
ubuntu@ubuntu:~$ ls -l /usr/local/bin/aws
Construct the install command using this symlink and directory information and then confirm the installation using the commands below:
ubuntu@ubuntu:~$ aws --version
Installing Session Manager Plugin:
Install the Session Manager plugin on your local computer if you wish to use the AWS CLI to start and end sessions. To install this plugin on Linux, first, download the RPM package and then install it using the following sequence of commands:
ubuntu@ubuntu:~$ sudo yum install -y session-manager-plugin. rpm
After installing the package, you can confirm whether the plugin is installed successfully or not using the following command:
OR
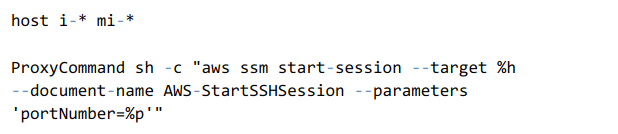
Updating the local host SSH configuration file:
Change the SSH configuration file to allow a proxy command to start a session of the Session Manager and pass all data via the connection. Add this code to the SSH configuration file paced at “~/.ssh/config”:
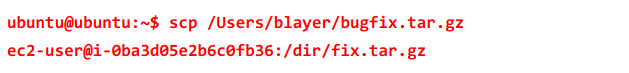
Using SCP and SSH:
Now you will be prepared to dispatch SSH and SCP connections with your cloud properties straightforwardly from your nearby PC after the previously mentioned steps are finished.
Get the cloud asset instance-id. This can be achieved through the AWS management console or the following command:
SSH can be executed as usual by using the instance-id as the hostname, and the SSH command Line switches like this:
Now files can be transferred easily to the remote machine without any need of an intermediate stage, using SCP.
Conclusion:
Users have relied on firewalls for years to access cloud content safely, but these options have encryption and management overhead issues. While changeless infrastructure is an ideal objective for various reasons, in certain cases, creating or maintaining a live system needs copying patches or other data to the live instances, and many will end up with a need to get to or adjust systems running live. The AWS Systems Manager Session Manager permits this capability without extra firewall entrance and the need for external solutions like intermediate S3 use.