What Will We Cover?
In this guide, we will see how to use the “IAM Passrole” permission. As a specific example, we will see how to connect an EC2 instance with the S3 bucket using the passrole permission.
Important Terms and Concepts
AWS service role: It is a role assumed by a service so that it can perform the tasks on behalf of the user or account holder.
AWS service role for an EC2 instance: It is a role assumed by an application running on an Amazon EC2 instance to perform the tasks in the user account that are allowed by this role.
AWS service-linked role: It is a role that is predefined and directly attached to an AWS service, like the RDS service-linked role for launching a RDS DB.
Using the Passrole Permission to Connect an EC2 Instance with S3
Many AWS services need a role for configuration and this role is passed/administered to them by the user. In this way, services assume/take the role and perform the tasks on behalf of the user. For most services, the role needs to be passed once while configuring that service. A user requires permissions for passing a role to an AWS service. This is a good thing from a security point of view since the administrators can control which users can pass a role to a service. The “PassRole” permission is granted by a user to its IAM user, role, or group for passing a role to an AWS service.
To elaborate the previous concept, consider a case when an application running on an EC2 instance requires an access to the S3 bucket. For this, we can attach an IAM role with this instance so that this application gets the S3 permission defined in the role. This application will need the temporary credentials for authentication and authorization purposes. EC2 gets temporary security credentials when a role associates with the instance running our application. These credentials are then made available to our application to access S3.
To grant an IAM user the capability to pass a role to the EC2 service at the time of launching an instance, we need three things:
- An IAM permissions policy for the role that decides the scope of the role.
- A trust policy attached to the role which allows the EC2 to assume the role and use the permissions defined inside the role.
- An IAM permission policy for the IAM user that lists the roles which it can pass.
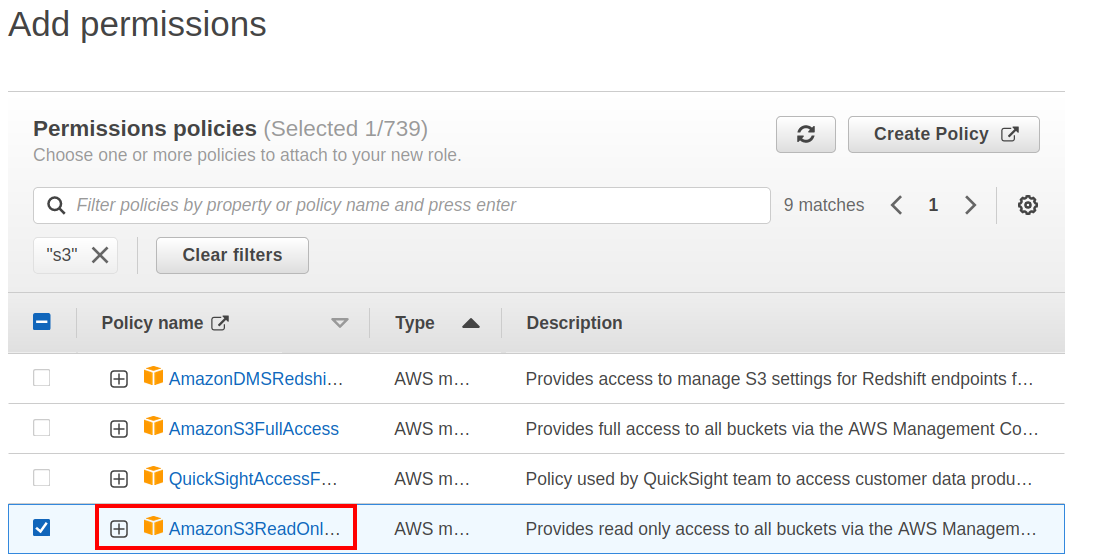
Let’s do it in a more pragmatic way. We have an IAM user with a limited permission. We then attach an inline policy to launch the EC2 instances and permission to pass an IAM role to a service. Then, we create a Role for S3 access; let’s call it “S3Access”. And attach an IAM policy to it. In this role, we only allow the reading of the S3 data using the AWS managed “AmazonS3ReadOnlyAccess” policy.
Steps to Create the Role
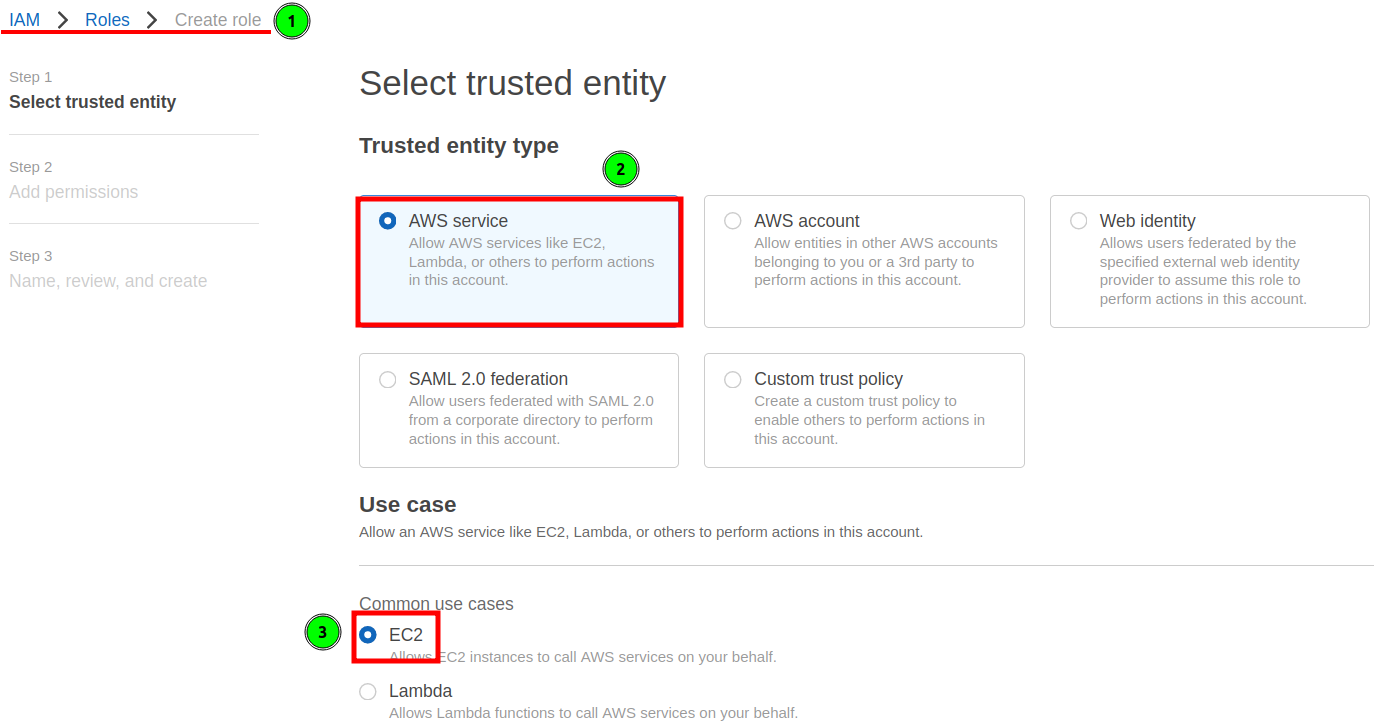
Step 1. From the IAM console of the administrator (root), click on “Role” and then select “Create role”.
Step 2. From the “Select trusted entity” page, select “AWS service” under the “Trusted entity type”.
Step 3. Under the “Use case”, select the radio button corresponding to the “EC2” for the “Use cases for other AWS services”:
Step 4. On next page, assign an “AmazonS3ReadOnlyAccess” policy:
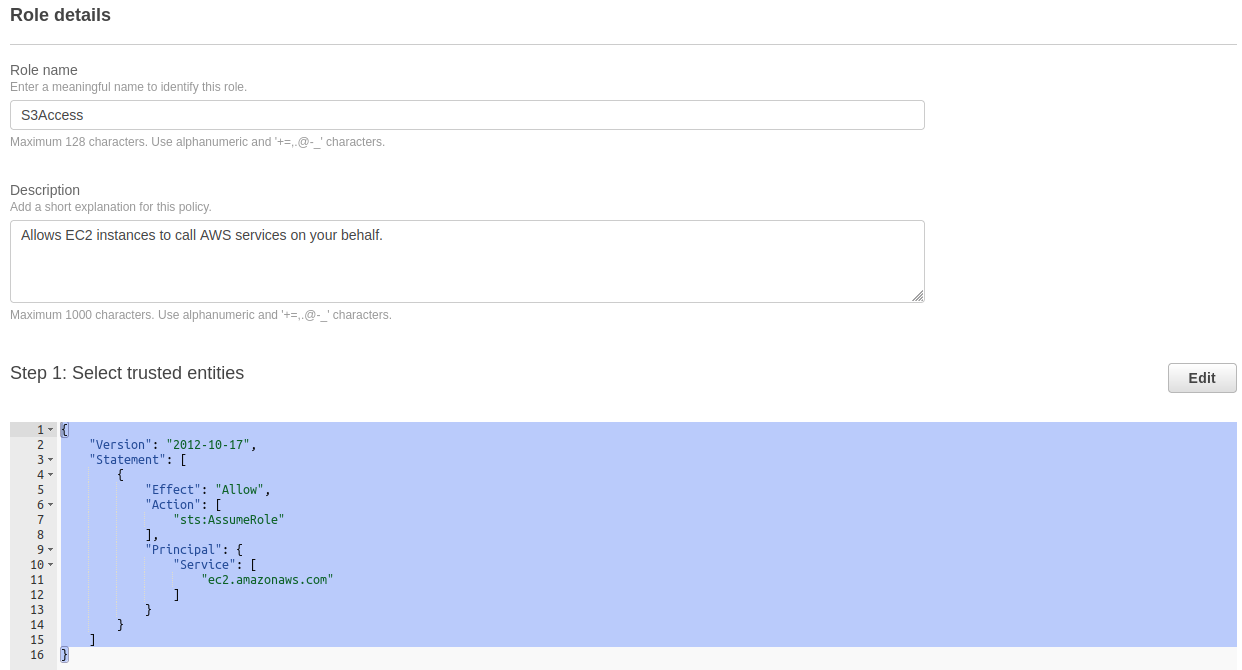
Step 5. Give a name to your role (“S3Access” in our case). Add a description for this role. The following trust policy is automatically created with this role:
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"sts:AssumeRole"
],
"Principal": {
"Service": [
"ec2.amazonaws.com"
]
}
}
]
}
Step 6. Click on “Create role” to create the role:
IAM Policy for User
This policy gives the IAM user full EC2 permissions and permission to associate the “S3Access” role with the instance.
Step 1. From the IAM console, click on Policies and then on “Create policies”.
Step 2. On the new page, select the json tab and paste the following code:
"Version": "2012-10-17",
"Statement": [{
"Effect":"Allow",
"Action":["ec2:*"],
"Resource":"*"
},
{
"Effect":"Allow",
"Action":"iam:PassRole",
"Resource":"arn:aws:iam::Account_ID:role/S3Access"
}]
}
Replace the bolded text “Account_ID” with the user Account ID.
Step 3. (Optional) Give tags for your policy.
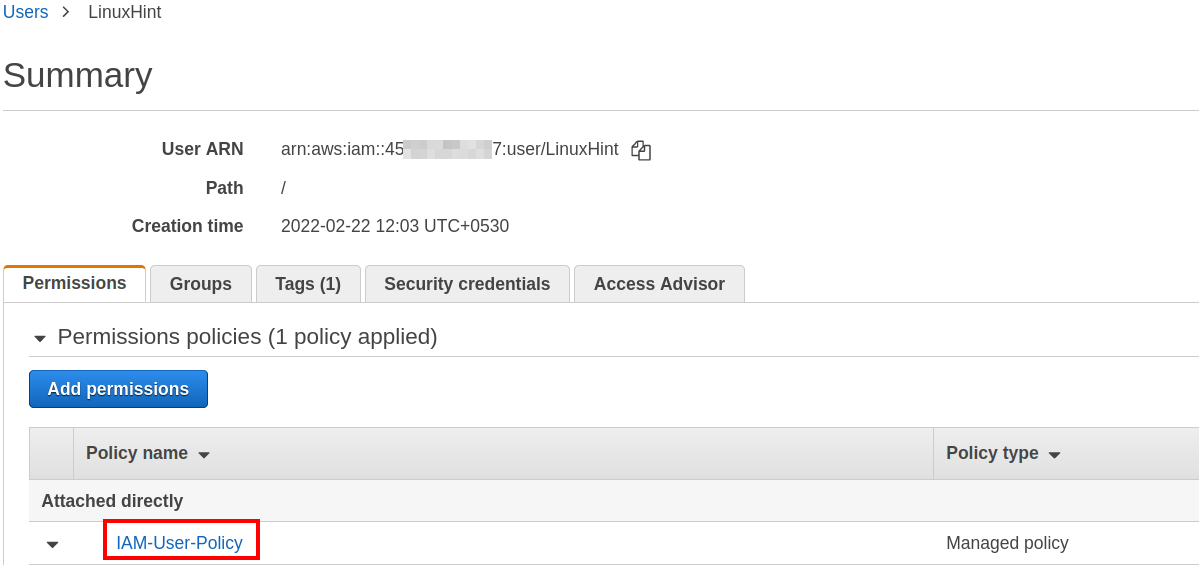
Step 4. Put a suitable name for the policy (“IAM-User-Policy” in our case) and click the “Create policy” button and attach this policy to your IAM user.
Attaching the “S3Access” Role to the EC2 Instance
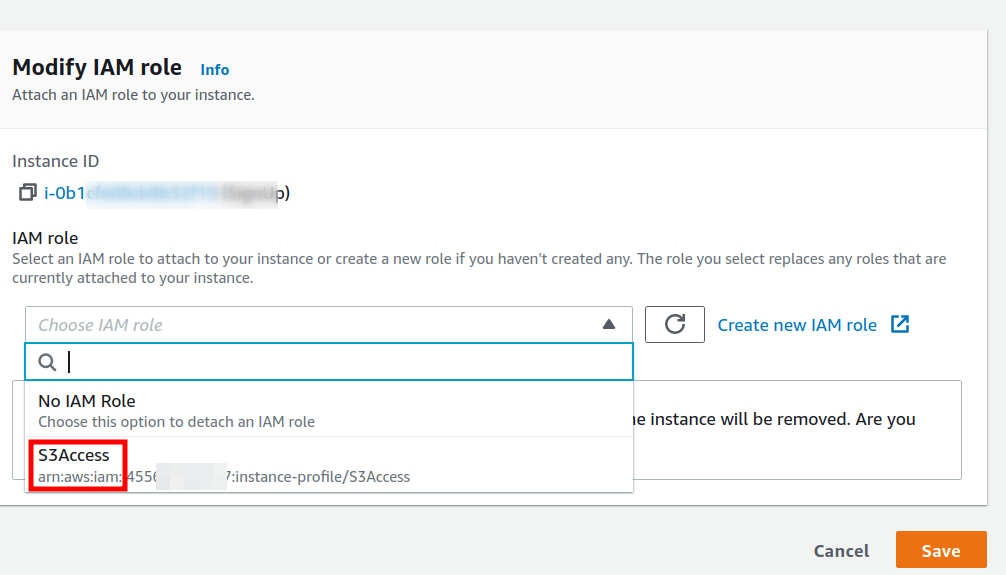
Now, we will attach this role to our instance. Select your instance from the EC2 console and go to “Action > Security > Modify IAM role”. On the new page, select the “S3Access” role from the drop down menu and save it.
Verifying the Setup
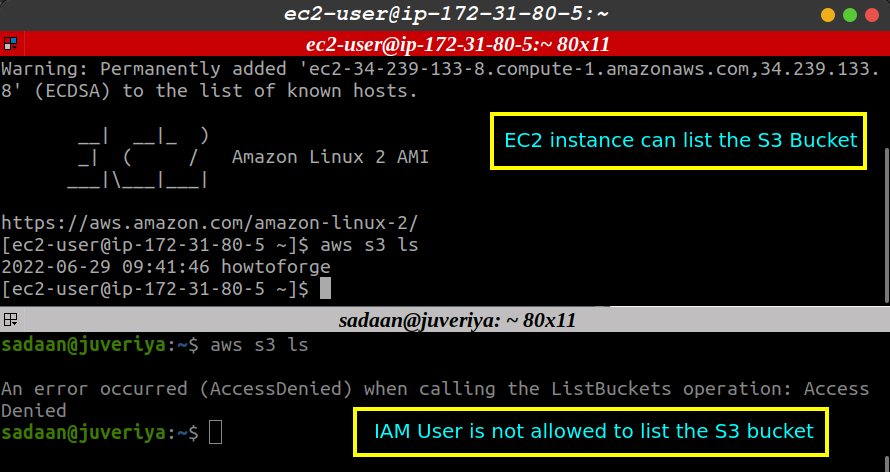
Now, we will check if our EC2 instance is able to access our S3 bucket created by the administrator. Login into the EC2 instance and install the AWS CLI application. Now, run the following command on this EC2 instance:
Again, run the previous command from the IAM account configured on your local machine. You will notice that the command is successfully executed on the EC2 instance but we got an “access denied” error on the local machine:
The error is obvious because we have only granted the S3 access permission for the EC2 instance but not to the IAM user and to any other AWS service. Another important thing to note is that we did not make the bucket and its objects publicly accessible.
Conclusion
In this guide, we demonstrated how to use the PassRole permission in AWS. We successfully managed to connect the EC2 to S3. It is a very important concept if you care about granting the least privileges to your IAM users.