This article aims to explore the issues associated with “Invoke-Expression” and discuss more secure alternatives when scripting in PowerShell.
What is Invoke-Expression?
“Invoke-Expression” is a cmdlet in PowerShell that evaluates and executes commands stored in a string. It provides a way to run dynamically generated code during a script’s execution. This flexibility allows developers to create customizable scripts based on user input or condition-based logic:
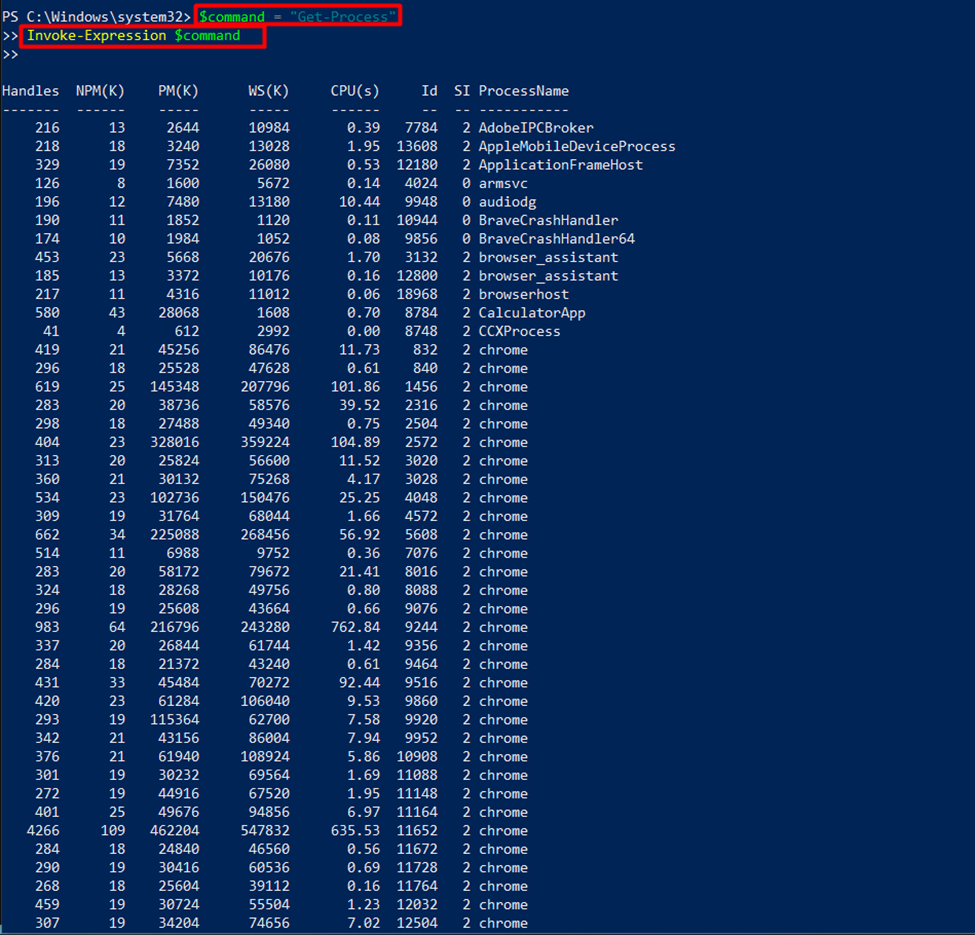
Invoke-Expression $command
In this case, the variable “$command” holds a string representing a PowerShell command. “Invoke-Expression” then executes the command stored in the string, resulting in the output of the “Get-Process” cmdlet.
Issues with Invoke-Expression
Some of the issues by using “Invoke-Expression” are mentioned below:
Now, let’s discuss these issues in detail.
1. Security Risks
“Invoke-Expression” poses significant security risks, primarily due to its potential to execute malicious or unintended code. If an attacker manages to inject malicious commands into the string that “Invoke-Expression” executes, it can lead to unauthorized access, data breaches, or system compromises. Without adequate input validation and filtering, the risk of code injection becomes substantial.
2. Code Execution Control
One of the critical issues with “Invoke-Expression” is its lack of control over code execution. When using “Invoke-Expression”, it becomes challenging to track and limit access to sensitive resources or commands executed by the invoked code. This lack of control could lead to unintended behavior or unauthorized access if exploited.
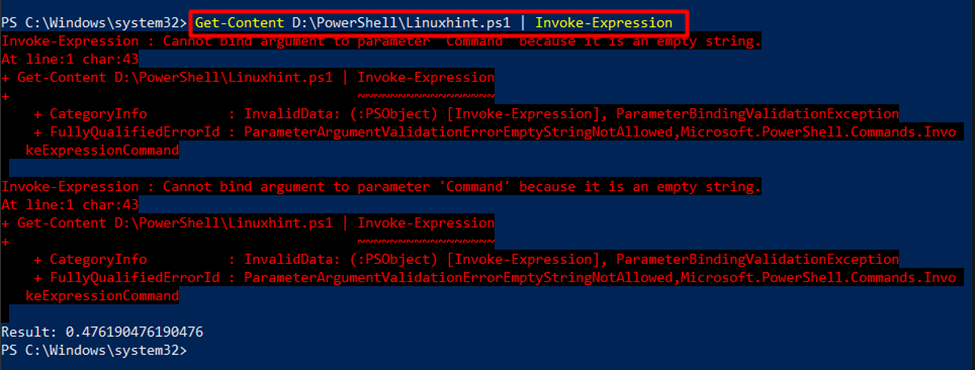
For instance, the below command shows an error when the “Invoke-Expression” cmdlet is executed showing limited access to fulfill the Get-Content cmdlet.
In the example above, we get an error while executing the statement.
3. Performance Drawbacks
Using “Invoke-Expression” imposes a performance overhead due to its need to parse and evaluate strings as code at runtime. This parsing introduces unnecessary runtime delays, impacting script execution time and overall system performance.
4. Unnecessary Complexity
“Invoke-Expression” often necessitates the use of complicated string manipulation methods to construct commands dynamically. As a result, code readability and maintainability suffer, making it challenging for developers to understand, debug, and modify scripts that extensively utilize this cmdlet.
Best Practices for Avoiding Invoke-Expression
To minimize the security risks associated with “Invoke-Expression”, PowerShell practitioners should adhere to a set of best practices. These practices include:
1. Invoke-Command
A safer alternative to “Invoke-Expression” is the “Invoke-Command” cmdlet, which allows remote execution of commands on a target system. By using “Invoke-Command” with proper authentication and authorization mechanisms, administrators can achieve secure and controlled execution of arbitrary commands or scripts:
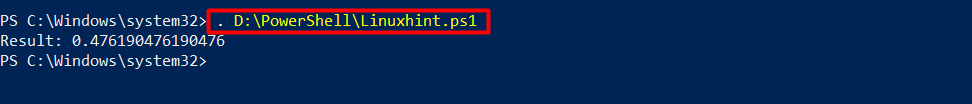
2. Dot Sourcing
“Dot Sourcing” offers a more secure approach compared to “Invoke-Expression” when executing code from external files. By using a dot followed by a space and the file path, PowerShell can import and execute the commands within the file. This technique provides greater visibility and control over the content being executed:
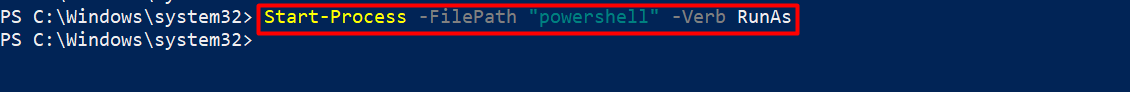
3. Start-Process
To mitigate the security vulnerabilities associated with “Invoke-Expression”, the “Start-Process” cmdlet offers a safer option for executing external processes or scripts. Start-Process allows developers to specify executable files or script paths directly, without relying on command strings, ensuring a more controlled and secure execution environment.
Starting a PowerShell session as an administrator:
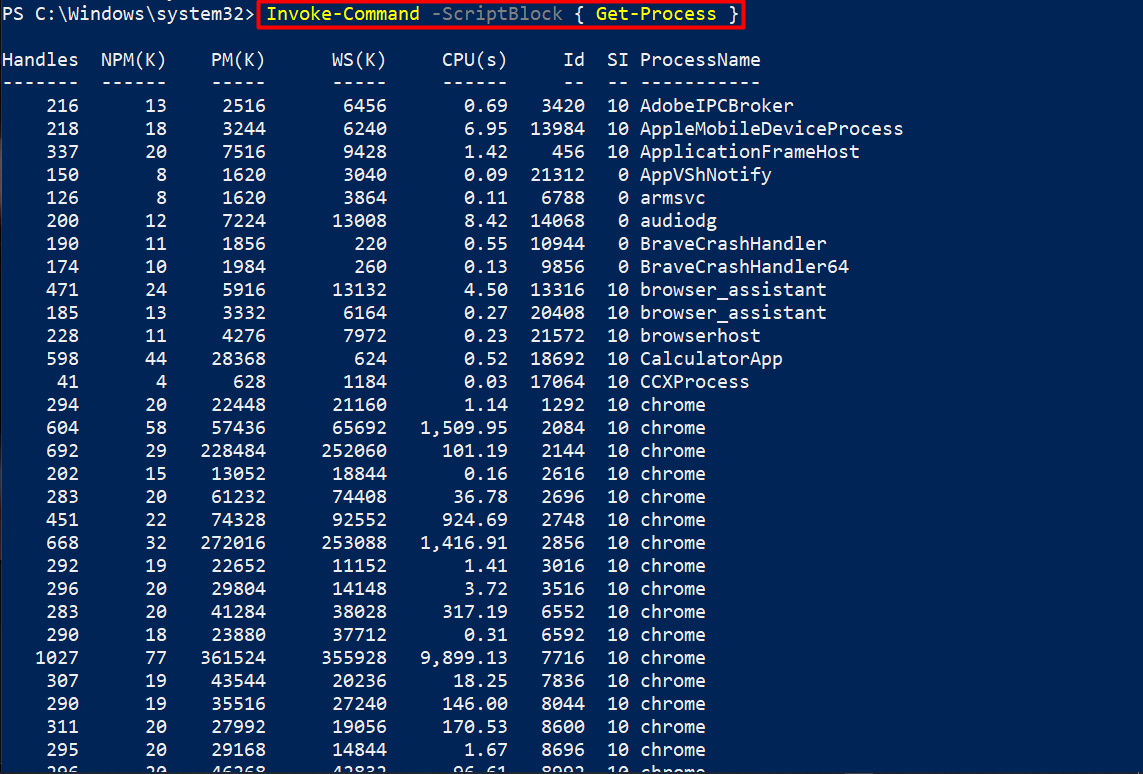
4. Script Blocks
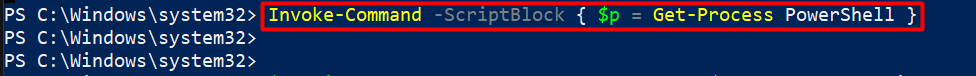
In the scenarios where dynamic code execution is needed, PowerShell “script blocks” provide a safer alternative to “Invoke-Expression”. By encapsulating the desired code within a script block, developers can delay its execution until explicitly called, ensuring greater control over the commands being executed.
The “Invoke-Command” cmdlet takes a “ScriptBlock” parameter that takes “Get-Process” as a value:
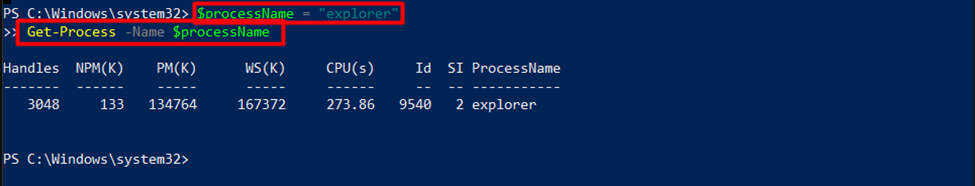
5. Parameterized Commands
When dealing with dynamic code, consider parameterizing commands instead of using “Invoke-Expression”. By passing arguments as parameters to cmdlets or functions, you can maintain security and readability while achieving the desired dynamic behavior. Instead of using “Invoke-Expression” on a string, create a script with arguments and invoke it directly since the script or code already exists in the file or AST form:
Get-Process -Name $processName
In this example, the “$processName” variable holds the desired process name, which is then passed as an argument to the “Get-Process” cmdlet. This approach avoids the risks associated with dynamic execution while providing flexibility.
Conclusion
While “Invoke-Expression” can be a convenient tool for executing dynamic code in PowerShell, its inherent security risks can lead to adverse consequences. By understanding these risks and adopting secure alternatives, such as “Invoke-Command”, “Dot Sourcing”, and “Script Blocks”, PowerShell practitioners can enhance their scripts’ security and maintain control over code execution.