AppArmor, a Linux Kernel Security Module, can restrict system access by installed software using application specific profiles. AppArmor is defined as Mandatory Access Control or MAC system. Some profiles are installed at the time of package installation and AppArmor contains some addition profiles from apparmor-profiles packages. The AppArmor package is installed on Ubuntu by default and all default profiles are loaded at the time of system start up. The profiles contain the list of access control rules which are stored in etc/apparmor.d/.
You can also protect any installed application by creating a AppArmor profile of that application. AppArmor profiles can be in one of two modes: ‘complain’ mode or ‘enforcement’ mode. The system does not enforce any rules and profile violations are accepted with logs when in complain mode. This mode is better to test and develop any new profile. The rules are enforced by the system in enforced mode and if any violation occurs for any application profile then no operation will be permitted for that application and the report log will be generated in syslog or auditd. You can access the syslog from the location, /var/log/syslog. How you can check the existing AppArmor profiles of your system, change the profile mode and create a new profile are shown in this article.
Check Existing AppArmor Profiles
apparmor_status command is used to view the loaded AppArmor profiles list with status. Run the command with root permission.
The profiles list can be varied according to the operating system and installed packages. The following output will appear in Ubuntu 17.10. It is shown that 23 profiles are loaded as AppArmor profiles and all are set as enforced mode by default. Here, 3 processes, dhclient, cups-browsed and cupsd are defined by the profiles with enforced mode and there is no process in complain mode. You can change the execution mode for any defined profile.
Modify Profile Mode
You can change the profile mode of any process from complain to enforced or vice versa. You have to install the apparmor-utils package to do this operation. Run the following command and press ‘Y’ when it ask for the permission to install.
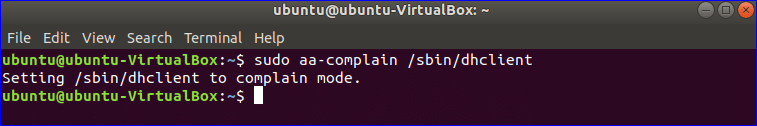
There is a profile named dhclient which is set as enforced mode. Run the following command to change the mode to complain mode.
Now, if you check the status of AppArmor profiles again then you will see the execution mode of dhclient is changed to complain mode.
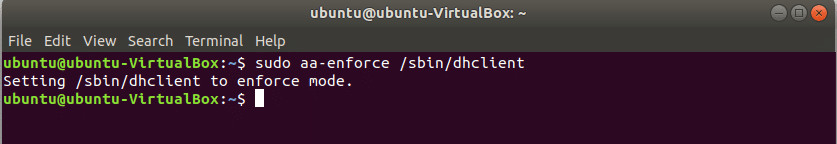
You can again change the mode to enforced mode by using the following command.
The path to set the execution mode for all AppArmore profiles is /etc/apparmor.d/*.
Run the following command to set the execution mode of all profiles in complain mode:
Run the following command to set the execution mode of all profiles in enforced mode:
Create a new profile
All installed programs don’t create AppArmore profiles by default. To keep the system more secure, you may need to create an AppArmore profile for any particular application. To create a new profile you have to find out those programs that are not associated with any profile but need security. app-unconfined command is used to check the list. According to the output, the first four processes are not associated with any profile and last three process are confined by three profiles with enforced mode by default.
Suppose, you want to create the profile for NetworkManager process which is not confined. Run aa-genprof command to create the profile. Type ‘F’ to finish the profile creation process. Any new Profile is created in enforced mode by default. This command will create an empty profile.
No rules define for any newly created profile and you can modify the content of the new profile by editing the following file to set restriction for the program.
Reload all profiles
After setting or modifying any profile you have to reload the profile. Run the following command to reload all existing AppArmor profiles.
You can check the currently loaded profiles by using the following command. You will see the entry for newly created profile of NetworkManager program in the output.
So, AppArmor is a useful program to keep your system safe by setting necessary restrictions for important applications.