This tutorial teaches you about Ansible secrets, mainly on Ansible Vault. You’ll know how to securely handle a sensitive data in your Ansible playbooks by the end.
What Is Ansible Vault?
Ansible Vault is a feature of Ansible that allows us to keep the sensitive data, such as passwords or keys, encrypted.
Once we run a playbook that uses one of the sensitive data that is stored in the vault, Ansible decrypts the data on the fly.
Ansible Vault offers two main advantages:
Security – The vault encrypts the data using AES-256 which ensures that the data is always secure.
Simplicity – The vault is tightly integrated with Ansible which makes using the encrypted data in playbooks easy.
Creating the Encrypted Files
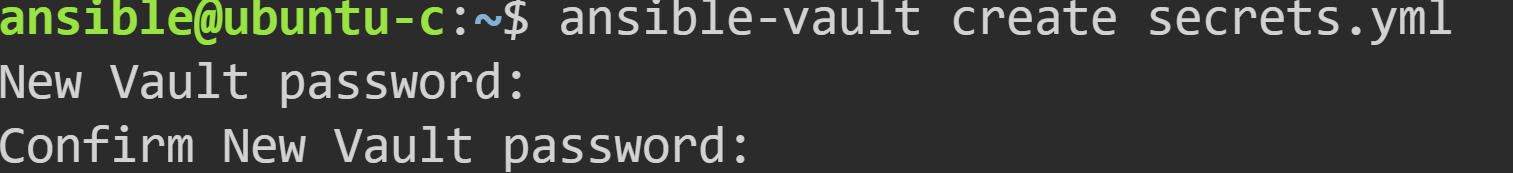
To create a new encrypted file, use the ansible-vault command as follows:
The previous command prompts you for a password. We use this password to view or edit the encrypted content.
Once you set the vault password, you will be launched into an editor window such as Vim or Nano which allows you to input your desired information.
api_key: abc123xyz789
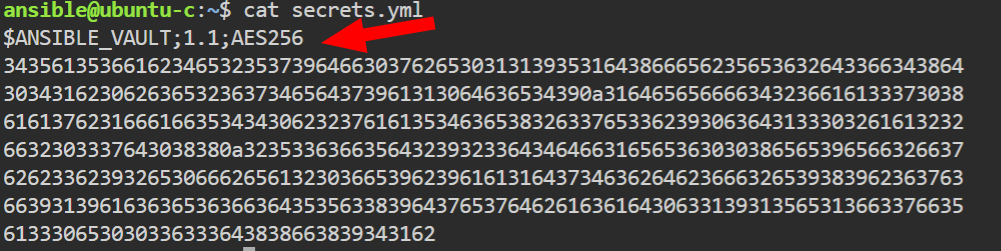
Save and exit it. This should create an encrypted file. You can use the cat command to confirm as follows:
Editing the Encrypted Files
To edit an encrypted file, use the edit command as shown in the following:
This prompts you for the vault password that you configured in the previous section. Once authenticated, Ansible opens the vault file with your default editor in decrypted form which allows you to configure the values of your file.
Once done, close and save the file, and Ansible will re-encrypt the data.
Using Encrypted Data in Playbooks
To use a playbook that utilizes the data that is stored in the vault, we can do it in two main ways. The first is an interactive mode which tells Ansible to prompt you for the vault’s password:
You can also define a password file which contains the password to the vault as follows:
$ chmod 600 .vault_pass.txt
Once created, you can pass the password file as follows:
The example playbook is as follows:
vars_files:
- secrets.yml
tasks:
- name: Print secret
debug:
var: db_password
Conclusion
We learned how to configure and use the Ansible Vault to manage the sensitive information while ensuring that they are easily accessible within Ansible playbooks.