Aireplay-ng is used to generate rogue Wireless traffic. It can be used along with aircrack-ng to crack WEP and WPA keys. The main purpose of aireplay-ng is to inject frames. There are several different types of powerful attacks that can be performed using aireplay-ng, such as the deauthentication attack, which helps in capturing WPA handshake data, or the fake authentication attack, in which packets are injected into the network access point by authenticating to it to create and capture new IVs. Other types of attacks are included in the following list:
- Interactive packet replay attack
- ARP request replay attack
- KoreK chopchop attack
- Cafe-latte attack
- Fragmentation attack
Usage of aireplay-ng
Injection Test
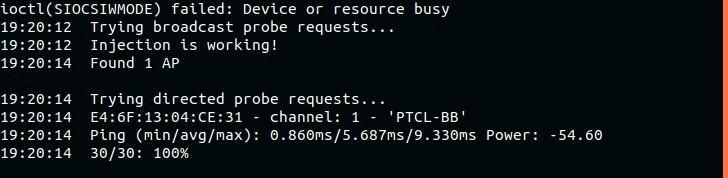
Certain network cards do not support packet injection, and aireplay-ng only works with network cards that support this feature. The first thing to do before performing an attack is to check whether your network card supports injection. You can do this simply by running an injection test using the following command:
-9 : Injection test (–test can also be used)
Wlan0: Network interface name
Here, you can see that we have found 1 AP (Access point), named PTCL-BB, the interface that is used, the ping time, and the channel it is running on. So, we can clearly determine by looking at the output that injection is working, and we are good to perform other attacks.
Deauthentication Attack
The deauthentication attack is used to send deauthentication packets to one or more clients who are connected to a given AP to deauthenticate the client(s). Deauthentication attacks can be performed for many different reasons, such as capturing WPA/WPA2 handshakes by forcing the victim to reauthenticate, recovering a hidden ESSID (hidden Wi-Fi name), generating ARP packets, etc. The following command is used to perform a deauthentication attack:
-0 : Deauthentication attack
1 : Number of deauthentication packets to send
-a : MAC address of AP (Wireless Router)
-c : MAC address of victim (if not specified, it will deauthenticate all the clients connected to the given AP)
wlan0 : Network interface name
As you can see, we have successfully deauthenticated the system with the given MAC address that was connected just a moment before. This deauthentication attack will force the specified client to disconnect and then reconnect again to capture the WPA handshake. This WPA handshake can be cracked by Aircrack-ng later on.
If you do not specify the ‘-c’ option in the above command, aireplay-ng will force every device on that Wireless router (AP) to disconnect by sending fake deauthentication packets.
Fake Authentication Attack (WEP)
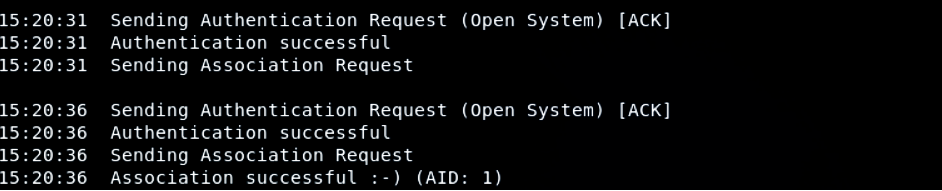
Suppose that you need to inject packets into an AP (Wireless Router), but you do not have your client device associated or authenticated with it (this only works in the case of WEP security protocol). APs contain a list of all connected clients and devices and they ignore any other packet coming from any other source. It will not even bother to see what is inside the packet. To tackle this issue, you will authenticate your system to the given router or AP through a method called fake authentication. You can perform this action using the following commands:
-1 : Fake authentication attack (–fakeauth can also be used)
-a : Access Point MAC address
-h : MAC address of the device to which to perform fake authentication
wlan0 : Network interface name
In the above output, you will see that the authentication request was successful and the network has now become an open network for us. As you can see, the device is not connected to the given AP, but rather, authenticated to it. That means that packets can now be injected into the specified AP, as we are now authenticated, and it will receive any request we will send.
ARP Request Replay Attack (WEP)
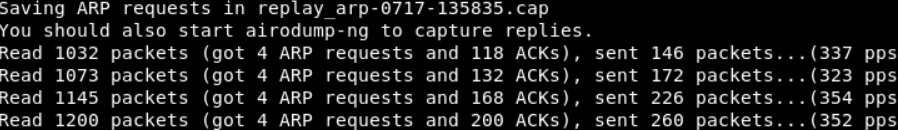
The best and most reliable way to produce new initialization vectors is the ARP request replay attack. This type of attack waits and listens for an ARP packet and, on obtaining the packet, transmits the package back. It will continue to retransmit ARP packets back again and again. In each case, a new IV will be generated, which later helps in cracking or determining the WEP key. The following commands will be used to perform this attack:
-3 : Arp request replay attack (–arpreplay can also be used)
-b : MAC address of AP
-h : MAC address of the device to which the fake authentication is to be sent
wlan0 : Network interface name
Now, we will wait for an ARP packet from the Wireless AP. Then, we will capture the packet and re-inject it into the interface specified.
This produces an ARP packet and that must be injected back, which can be done using the following command:
-2 : Interactive frame selection
-r : Name of file from last successful packet replay
Wlan0: Network interface name
Here, airodump-ng will be started to capture the IVs, first putting the interface in monitor mode; meanwhile, the data should start increasing rapidly.
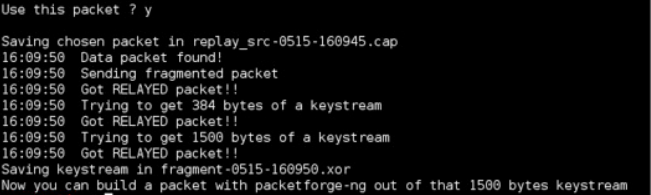
Fragmentation Attack (WEP)
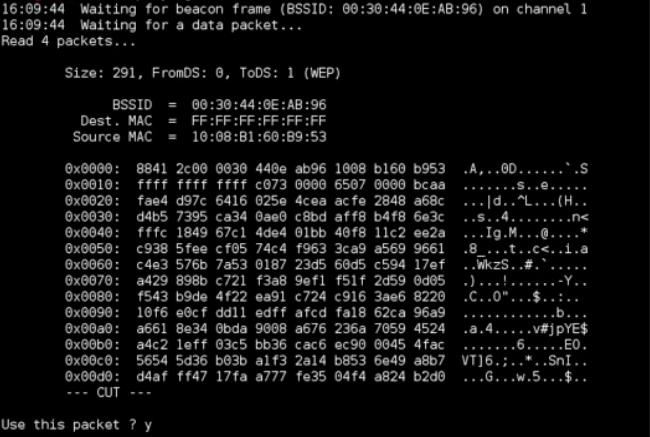
A fragmentation attack is used to get 1500 bytes of P-R-G-A, rather than a WEP key. These 1500 bytes are later used by packetforge-ng to perform various injection attacks. A minimum of one packet obtained from the AP is required to obtain these 1500 bytes (and sometimes less). The following commands are used to perform this type of attack:
-5 : Fragmentation attack
-b : MAC address of AP
-h : MAC address of the device from which packets will be injected
wlan0 : Network interface name
After capturing the packet, it will ask whether to use this packet to obtain the 1500 bytes of PRGA. Press Y to continue.
Now we the 1500 bytes of PRGA have successfully been obtained. These bytes are stored in a file.
Conclusion
Aireplay-ng is a useful tool that helps in cracking WPA/WPA2-PSK and WEP keys by performing various powerful attacks on wireless networks. In this way, aireplay-ng generates important traffic data to be used later on. Aireplay-ng also comes with aircrack-ng, a very powerful software suite consisting of a detector, a sniffer, and WPA and WEP/WPS cracking and analysis tools.