Common Challenges Faced in Metasploit
1. Installation and Setup Problems
One of the initial challenges faced by numerous users involves the installation and setup procedure. Metasploit relies on various dependencies that require a precise configuration. If this setup isn’t executed correctly, it can result in various problems, including the absence of modules or components that don’t function as intended.
Solution:
Verify the Dependencies: Make certain that all necessary dependencies are installed and kept current. Metasploit’s official documentation offers a detailed list of prerequisites that are tailored to various operating systems. Execute a full update and upgrade of your Linux system by employing the following command:
Use a Penetration Purpose Linux Distro: To streamline the setup process, consider using a Penetration Linux distro such as Kali Linux which comes with Metasploit pre-installed.
2. Database Connection Errors
Metasploit relies on a database to store the information about targets, vulnerabilities, and session data. Connection issues with the database can hinder your testing workflow.
Solution:
Database Configuration: Ensure that your database settings in Metasploit are correctly configured. Double-check the credentials, host addresses, and ports.
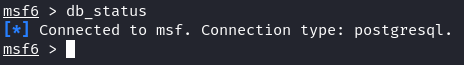
Database Maintenance: Regularly maintain your database by running the “db_status” command to check the connection status.
3. Module Compatibility Problems
Metasploit modules are crucial for successful exploitation. Incompatibility issues can arise when using modules that do not match the target system’s configuration.
Solution:
Module Validation: Always validate the compatibility of modules with the target system. Use the “check” command to verify whether a particular module is suitable for the target.
Module Customization: If necessary, customize the existing modules or create your own to fit the target environment.
4. Firewall and Antivirus Interference
Firewalls and antivirus software can block Metasploit’s traffic and prevent a successful exploitation.
Solution:
Payload Encryption: Employ the payload encryption and obfuscation techniques to evade detection by security software.
Port Scanning: Use tools like Nmap to perform a stealthy port scanning before launching Metasploit to avoid drawing attention to your activities.
5. Session Stability Issues
Once a successful exploit is executed, maintaining a stable session is essential for post-exploitation activities. Session loss can disrupt your progress.
Solution:
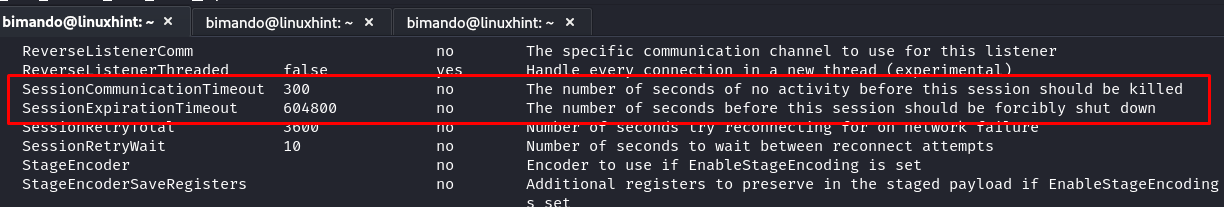
Session Keep-Alive: Configure the session keep-alive settings to ensure stable connections. Metasploit offers advanced options to maintain the sessions by setting the “SessionCommunicationTimeout” and “SessionExpirationTimeout” values to be longer. To see the advanced options in msfconsole windows, type the following:
That advanced setting has default values that you can customized. To extend the “SessionCommunicationTimeout” and “SessionExpirationTimeout” values, you could just type the following:
msf> set SessionExpirationTimeout <higher value>
Session Pivoting: Implement the session pivoting techniques to maintain an access even if the initial session is lost.
6. Exploitation Failures
Despite careful planning, not all exploitation attempts succeed. Understanding why an exploit failed is critical for effective troubleshooting.
Solution:
Log Analysis: Analyze Metasploit’s logs for error messages and hints on why an exploit failed. Logs can provide valuable insights into what went wrong.
Alternative Exploits: If one exploit fails, consider trying the alternative exploits or different attack vectors.
7. Resource Intensiveness
Metasploit can be resource-intensive, leading to system slowdowns or crashes, especially during extensive scans or attacks.
Solution:
Resource Management: Allocate sufficient system resources (CPU, RAM) to Metasploit to prevent a resource exhaustion. Consider running Metasploit on dedicated machines or virtualized environments.
Throttling: Use the throttling options to limit the rate of exploitation attempts, reducing the strain on the target system.
Conclusion
In the realm of penetration testing, mastering Metasploit is a journey filled with challenges and triumphs. This guide provided insights into the common issues that are faced during penetration testing with Metasploit and offered practical solutions to overcome them. Remember that troubleshooting is an essential skill for any cybersecurity professional. By persistently refining your troubleshooting abilities, you’ll be better equipped to navigate the complex world of ethical hacking and secure the digital landscape.