“A Virtual Private Network or VPN allows you to extend a private network across public networks. It enhances your online security; for example, if you are at a hotel and you are using the hotel’s internet connection for your business, there is a high chance that your data may be breached. VPN connections are private and encrypted, which prevents unauthenticated access to your connection. Today in this tutorial, we will go through all the steps required to set up OpenVPN Server on Ubuntu 22.04.”
OpenVPN
OpenVPN is an open-source application that is mainly used to access remote websites, create secure connections, and enhance security by using encryption, authentication, and of course, certification using the OpenSSL library. We will now set up OpenVPN on Ubuntu 22.04.
Step 1: Update the System Packages
And it will automatically update your system’s packages.
Step 2: Install OpenVPN
Now you have to wait a while, and once it is done, you can move to step 3.
Step 3: Generate a Static Key to Use for VPN Tunnel Encryption and Start the VPN Server
Note: You may have noticed the “&” at the end of the command above, and it is there to help you background the OpenVPN process so that you don’t have to keep the terminal open.
Step 4: Verify if You are Going True
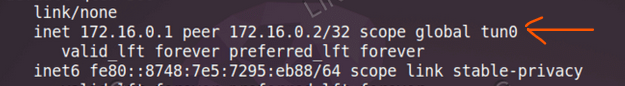
Just enter the following command, and you will tun0 with an IP address of 172.16.0.1
The output would be like this
Now we have to verify if the UDP port 1194 is open for connections using the following command
And this would generate output like this
Step 5: Configure Firewall
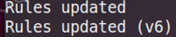
Use the following command to configure the firewall
And you will see the following output
The OpenVPN server is now capable of receiving incoming connections.
Now how are you going to connect the OpenVPN server from a remote client? Well, you have to go through the following steps.
Step 1: Install OpenVPN
Step 2: Transfer the static-OpenVPN Key File From the OpenVPN Server to the Client
First, we have to transfer the file from the server to the client using a secure method of your choice, but we will use the SCP command like this
Note: this command needs to be issued from the client side, and do use your username.
Step 3: Establishing a VPN Tunnel to the Server
Using the following command, we will be able to establish a VPN tunnel to the server, but you do need to change the IP address according to the server you are connecting to
Did you notice the cipher AES-256-CBC? Well, that is the most secure encrypting and decrypting the string of data.
Step 4: Testing if the Connection was Successful
If you are done with step 3, then you should be able to see the following message if the connection was successful.
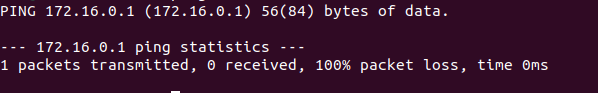
Now we will confirm the successful connection by pinging a host on the remote server using the following command
We will see something like this but don’t worry if it is different on your side
Conclusion
In this tutorial, we’ve gone through all the steps required to receive incoming connections using OpenVPN, and we also learned how to connect to an OpenVPN server from a remote client on Ubuntu. If you face any error or problem, please contact us because we are always happy to help our community.