SSH stands for Secure Shell, and as its name is saying, it is used to establish a secure connection between the client and its server. By default, every Linux based operating system supports SSH. SSH protocol is typically used for accessing, commanding, and transferring files remotely. So, in this post, you will demonstrate to generate SSH keys and use them to protect the server and precious information.
SSH Key Generation
When we generate an SSH key pair, it is generated in two steps. One is the creation of an SSH key on the client-side, and the second is copying it to the server or any remote host. A key pair consists of Private and Public key files named id_rsa and id_rsa.pub respectively in the ~/.ssh directory.
The IP address of my client system is
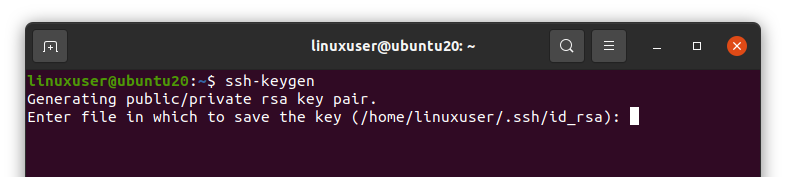
An SSH key can be generated by running the “ssh-keygen” command in the terminal.
It will ask you to enter the file name in which you want to save the private and public key, or you can go with the default selected files “id_rsa” and “id_rsa.pub” in the “.ssh” directory (/home/user/.ssh/id_rsa). Press Enter to select the default provided file.
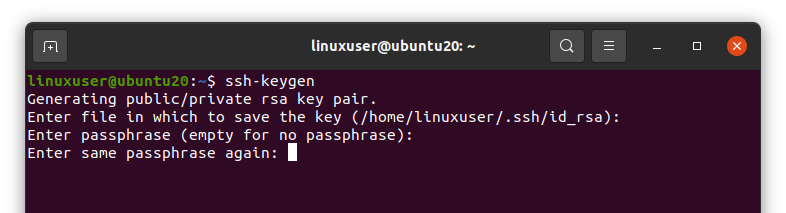
Next, it will ask for the Passphrase. A passphrase is actually kind of an extra security layer for securing the connection between host and client. When you log in to the host, it will ask for the passphrase again. So either enter the passphrase, or you can leave it empty and hit Enter without providing any passphrase.
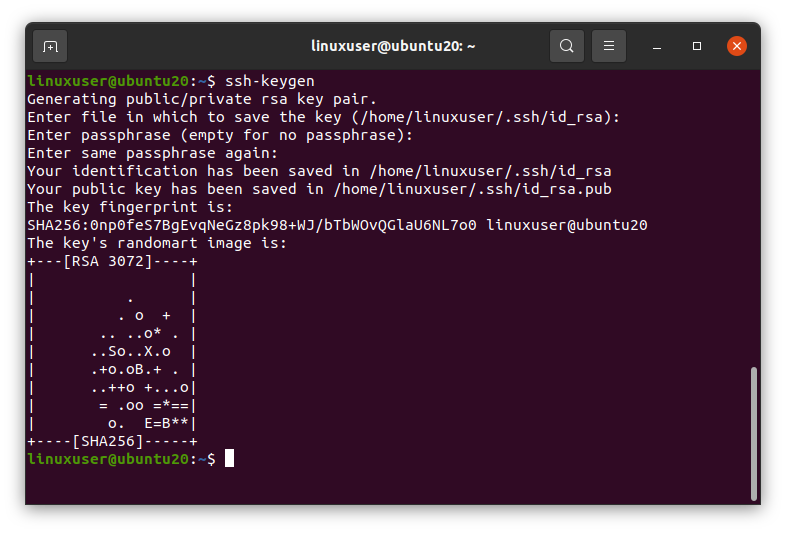
Once you are done with the passphrase, the SSH key should be generated.
You can notice in the screenshot that the generated Key is “RSA 3072”. What does that mean?
Algorithm Type and Size of SSH key
By default, the generated key’s algorithm type is RSA, and its bit size is 3072 bit. But you can change it if you want.
There are three major types of Algorithm for generating SSH keys.
RSA – Rivest Shamir Adleman. It is a key with a minimum size of 2048, and it is based on the difficulty of factoring large numbers.
DSA – Digital Signature Algorithm. This key is mostly used with 1024 size.
ECDSA – Elliptic Curves Digital Signature Algorithm. It supports 256, 384, and 521 bits.
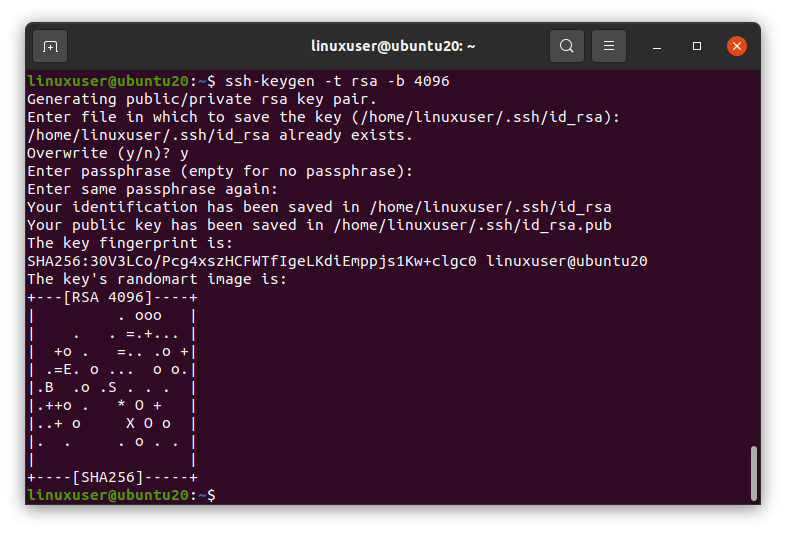
Now, if you want to provide your desired algorithm type and bit size, you can provide the algorithm type followed by the -t phrase after the ssh-keygen command, and you can also provide the bit size along with it followed by the -b phrase. The example is as follows,
As you can see in the screenshot, the key’s algorithm type is RSA, and the bit size is 4096. That’s great.
Copying the SSH key to the Host
You can simply copy the SSH key to the host by running the command given below in the client’s terminal.
Make sure to replace the username and host-ip-address with your user name and host’s IP address. My host’s user name and IP address is
IP Address: 192.168.18.131
You may face an error of connection refused by port 22 at this stage. In case of error, kindly visit our dedicated article (How to fix: Connection refused by port 22 Debian/Ubuntu – Linux Hint) for handling such error.
After running the above command, it will confirm from you to continue the connection; type “yes” to continue.
Once it is copied successfully, you are ready to log in to the server’s machine using the SSH key.
Log In to the Server
After successfully copying the SSH key to the host, we can log in to the host using the ssh command and by providing the username and IP address of the host using the following syntax.
Don’t forget to replace the user name and IP address with your host’s user name and IP address.
And here you are logged in to the host’s machine now if you type the “ip a” command in the terminal.
It will show the IP address of the host machine because you are on the server right now.
Wrap Up
This is how you can generate SSH keys, copy them to the host machine and access the host using the SSH keys. Thank you so much!