“One of the two most critical lines of defense that Linux networks and systems rely on is authentication. It is a standard term for logging into a system, commonly via sysadmin. And as a Linux user or administrator, this is certainly something you need to know and understand.
Of course, Linux authentication systems are vital, and there is often the need to understand how to implement them correctly.
This article acts as your introduction to Linux authentication systems. So, we will highlight the five user authentication methods every Linux user should know. We will also introduce you to various Linux authentication systems. We will briefly discuss Kerberos, SASL, SSH, NIS, NIS+, and LDAP. And since nearly each of these systems.”
What is Authentication?
Authentication is the process by which computer systems identify users who can access the system, device, or network. It is an access control mechanism that identifies users through predetermined identities such as usernames and passwords.
Administrators can use authentication protocols to control what each user can or cannot access. By doing so, unauthorized users will not access sensitive information. For example, an administrator can control what user X can access without revealing any sensitive information related to user Y.
Authentication helps to deter cybercriminals from gaining access to your networks or systems. Unauthorized access will inevitably lead to data theft, regulatory breaches, and spam ware or malware. Adobe, Yahoo, and Equifax are among the top companies with recent histories of data breaches.
Common Types of Authentication
It is impossible to understand authentication systems without knowing the common types of authentication. Security teams always look into countermeasures to improve their techniques. This is in a bid to neutralize the constantly improving efforts of cybercriminals.
Without notable improvements, incident response strategies, and top-notch security systems, companies will not stand up to the authentication-related challenges of the 21st century.
The following are the top 5 authentication types every Linux administrator should know;
- Password-Based Authentication– Passwords are by far the most common types of authentication. They exist in the form of letters, special characters, or numbers. Admins and users must create complicated passwords consisting of a combination of options for maximum protection. But when using passwords, be on the lookout for lousy hygiene and phishing attacks, as this may weaken your security.
- Certificate-Based Authentication– This is another way that technologies can use to identify users, devices, or machines. These digital certificates are electronic documents with the same concept used in passports or passports. They contain each user’s public key and a digital signature—a certification authority issues these certificates, which come in handy in proving public-key ownership.
- Multi-Factor Authentication– This authentication method requires more than one independent way to identify users. MFAs add multiple layers of security. They include captcha tests, smartphone codes, fingerprints, and facial recognition. It comes in handy in preventing account hacks.
- Token-Based Authentication– These authentication types enable users to feed in their credentials only once. Once they do that, they will receive a unique string of encrypted characters (tokens) that they will then use to access protected systems. A digital token is sufficient proof that you have permission to access the systems.
- Biometric Authentication– This method uses an individual’s biometrics or unique biological features to allow access. The biometrics includes facial recognition, fingerprint scanners, voice recognition, and eye scanners.
Common Linux Authentication Systems
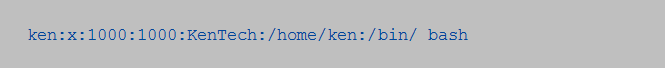
In Linux environments, authentication remains the formal syadmin requirement for logging into systems. And on most Linux platforms, /etc/passwd is often used for storing user information. The text file contains a user’s login, their password encryptions, a numerical unique user ID (UID), and a numerical group ID (GUD). The text file also contains the user’s home directory and preferred shell.
So, typical entries on /etc/passwd will often look closer to this;
As you will find out, an array of authentication and authorization systems is often used in the Linux realm. Each design comes in handy for a different purpose or application. But more interestingly, you can use more than a single authorization protocol in a single computing machine.
Even more, all these systems have a relationship with PAM, in one way or the other. That explains why we will first discuss PAM (Pluggable Authentication Modules).
PAM (Pluggable Authentication Modules)
PAM comprises a suite of shared libraries enabling local system administrators to choose how various applications can authenticate users. For example, a dedicated program will answer the call when a user connects to a serial port or network during program login. SSH will answer calls involving network connections and Getty for serial lines, while telnet can also answer calls relating to network connections.
Once any of the above programs answer a call, it will start a login program. It will log in and eventually request a username and a password for verification against the credentials in the /etc/passwd file. PAM often creates a layer of protection between an application and the actual authentication protocol.
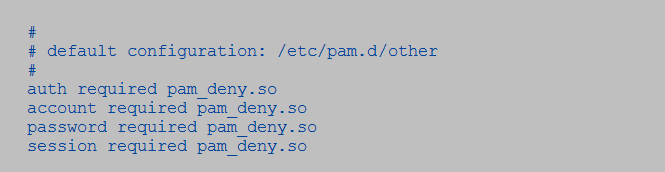
Still, PAM can support other authentication programs. But unlike common authentication programs, PAM can handle session and account data more accurately. For example, PAM can object access by normal users between 5.30 pm and 6.00 am. PAM files are available at /etc/pam.d.
An example of a PAM file configuration entry on a paranoid setting is;
The most significant Linux authentication systems include;
1. LDAP (Lightweight Directory Access Protocol)
As the name alludes, LDAP is a lightweight authentication protocol often used for accessing X.500 directory services, among others. It runs over transfer services such as IP/TCP or connection-oriented transfer modules.
LDAP protocol stores entries, which are collections of attributes with globally-unique Distinguished Names (DN). The sole purpose of the DN is to refer to each entry unambiguously. Besides, each attribute of an entry has a type and at least a single value.
In the above attribute, the type is a mail, while LINHINT.COM is the value.
The LDAP system works on a client-server model. It stands out as a mechanism through which clients can authenticate or prove their identities to directory servers and question the server. LDAP also plays a significant role in supporting privacy and security services.
2. SASL (Simple Authentication and Security Layer)
If you are looking for an authentication system for adding support and security to connection-based protocols, SASL is that kind of system. Often defined in RFC-2222, this authentication system includes a command that precisely identifies and authenticates users to servers and negotiates a security layer between this protocol and connections.
SASL helps users authenticate to servers without displaying their passwords in the open. While SASL can be used as an authentication-only protocol, it also comes in handy to check system or server integrity and encryptions. It is possible to integrate this system with PAM and the Kerberos protocol.
The default SASL library will resemble;
On the other hand, a sample server app included in the library will take this structure;
3. NIS and NIS+ (Network Information Service and Network Information Service Plus)
As the names suggest, these are simple network lookup services comprising databases and simple processes. The service changed its name from Sun Yellow Pages to Network Information Service due to copyright issues.
While the two function similarly, they have a name variation due to technological improvements. So, you can stick by NIS and only resort to NIS+ if you have dire security needs.
NIS and NIS+ will often distribute information, including;
- Login names or home directories and passwords (/etc/passwd)
- Hostnames and IP addresses (/etc/hosts)
- Group information (etc/group)
Usually, if you perform a lookup on the /etc/host.conf file, the result will provide you with the customized details of this line;
4. Kerberos
Kerberos is a reliable network authentication protocol popularly used to authenticate user or server applications using secret-key cryptography. Kerberos is a less vulnerable authentication tool than other Linux OS authentication systems.
It does not send unencrypted passwords over networks like most authentication systems. Besides, unlike other systems that rely on other client programs for reliability, Kerberos is pretty independent.
Kerberos provides credentials once you have an entry in the Kerberos database. Of course, an entry will include your Kerberos principal name and a password. And apart from providing credentials, Kerberos also provides the details of keytab files.
An entry for the host will look like this;
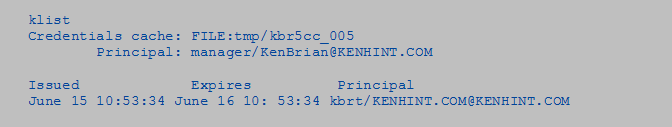
On the other hand, Kerberos credentials viewed using the klist command will take this form;
5. SSH (Secure Shell)
One of the most popular ways of accessing Linux systems is through the telnet program. But accessing shell accounts using telnet poses some danger because all your actions over the telnet program throughout the session will remain visible in plain text within your networks.
SSH comes as a solution that encrypts the data over local networks. It also provides an option for delivering networks with a choice of preventing passwords from being leaked over networks. The result is the elimination of information interception over systems and the eradication of impersonation of hosts.
While it can play various roles over a network, its primary function is to connect to remote hosts for terminal sessions. This command is often used;
Conclusion
The above is an introduction to Linux authentication systems. Of course, we will discuss all the five authentication protocols in other sections of this website in greater detail.