Kerberos remains one of the most secure authentication protocols in Linux environments. You will find out later that Kerberos also comes in handy for encryption purposes.
This article discusses how to implement the Kerberos service on Linux operating system. The guide will take you through the mandatory steps that ensures Kerberos service on a Linux system is successful.
Using Kerberos Service on Linux: An Overview
The essence of authentication is to provide a reliable process of ensuring that you identify all the users in your workstation. It also helps to control what users can access. This process is pretty difficult in open network environments unless you exclusively rely on signing on to each program by each user using passwords.
But in ordinary cases, users must key in passwords to access each service or application. This process can be hectic. Again, using passwords every time is a recipe for password leakage or vulnerability to cybercrime. Kerberos comes in handy in these instances.
Besides enabling users to register only once and access all the applications, Kerberos also allows the admin to continuously vet what each user can access. Ideally, using the Kerberos Linux successfully aims to address the following;
- Ensure that each user has their unique identity and no user takes someone else’s identity.
- Ensure that each server has its unique identity and proves it. This requirement prevents the possibility of attackers creeping in to impersonate servers.
Step By Step Guide On How to Use Kerberos in Linux
The following steps will help you use Kerberos in Linux successfully:
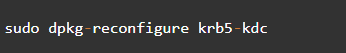
Step 1: Confirm If You Have KBR5 Installed In Your Machine
Check if you have the latest Kerberos version installed using the command below. If you do not have it, you can download and install KBR5. We already discussed the installation process in a different article.
Step 2: Create a Search Path
You will need to create a search path by adding /usr/Kerberos/bin and /usr/Kerberos/sbin to the search path.
Step 3: Set Up Your Realm Name
Your real name should be your DNS domain name. This command is:
You will need to modify the results of this command to fit your realm environment.
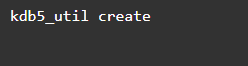
Step 4: Create and Start Your KDC Database for the Principal
Create a key distribution center for the principal database. Of course, this is also the point when you will need to create your master password for the operations. This command is necessary:
Once created, you can start the KDC using the below command:
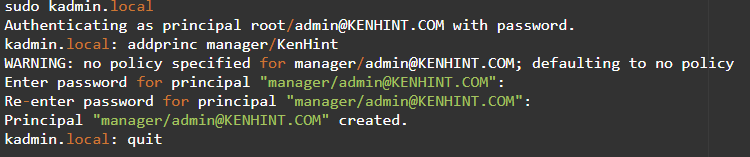
Step 5: Set Up a Personal Kerberos Principal
It is time to set up a KBR5 principal for you. It should have administrative privileges since you will need the privileges to administer, control, and run the system. You will also need to create a host principal for the host KDC. The prompt for this command will be:
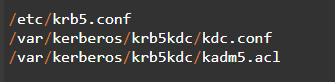
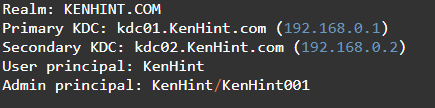
It is at this point that you may need to configure your Kerberos. Go to the default domain in the file “/etc/krb5.config” and input the following deafault_realm = IST.UTL.PT. The realm should also match the domain name. In this case, KENHINT.COM is the domain configuration required for the domain service in the primary master.
After completing the processes above, a window will show up that captures the summary of the network resources status up to this point, as shown below:
It is recommended that network validate users. In this case, we have KenHint should have a UID in a higher range than local users.
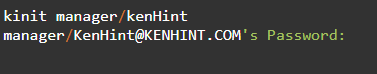
Step 6: Use the Kerberos Kinit Linux Command to Test New Principal
Kinit utility is used to test the new principal created as captured below:
Step 7: Create Contact
Creating contact is an incredibly vital step. Run both the ticket-granting server and the authentication server. The ticket-granting server will be on a dedicated machine which is only accessible by the administrator over the network and physically. Reduce all the networking services to the fewest possible. You should not even run the sshd service.
Like any login process, your first interaction with KBR5 will involve keying in certain details. Once you enter your username, the system will send the information to the Linux Kerberos authentication server. Once the authentication server identifies you, it will generate a random session for continued correspondence between the ticket-granting server and your client.
The ticket will usually contain the following details:
Names of both the ticket-granting server and the client
- Ticket lifetime
- Current time
- The new generation key
- The IP address of the client
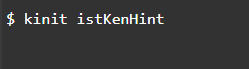
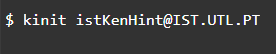
Step 8: Test Using the Kinit Kerberos Command to Obtain User Credentials
During the installation process, the default domain is set to IST.UTL. PT by the installation package. After that, you can obtain a ticket using the Kinit command as captured in the image below:
In the screenshot above, istKenHint refers to the user ID. This user ID will also come with a password for verifying if a valid Kerberos ticket exists. The Kinit command is used to show or retrieve the tickets and credentials present in the network.
After installation, you can use this default Kinit command to obtain a ticket if you do not have a custom domain. You can also customize a domain altogether.
In this case, the istKenHint is the corresponding network ID.
Step 9: Test the Admin System Using the Password Obtained Earlier
The documentation results are represented below after a successful run of the above command:
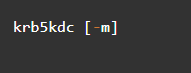
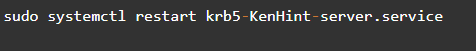
Step 10: Restart the kadmin Service
Restarting the server using the # kadmind [-m] command gives you access to the control list of users in the list.
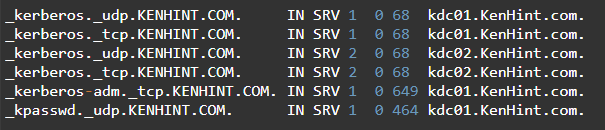
Step 11: Monitor How Your System Performs
The screenshot below highlights the commands added in /etc/named/db.KenHint.com to support clients in automatically determining the key distribution center for the realms utilizing the DNS SRV elements.
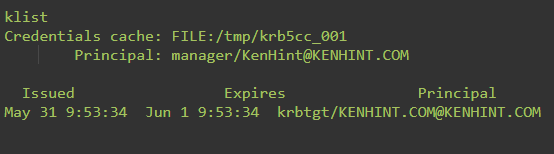
Step 12: Use the Klist Command to Examine Your Ticket and Credentials
After inputting the correct password, the klist utility will display the information below on the state of the Kerberos service that is running in the Linux system, as shown by the screenshot below:
The cache folder krb5cc_001 contains the denotation krb5cc_ and user identification as indicated in the earlier screenshots. You can add an entry to the /etc/hosts file for the KDC client to establish identity with the server as indicated below:
Conclusion
After completing the steps above, the Kerberos realm and services initiated by the Kerberos server are ready and running on the Linux system. You can continue using your Kerberos to authenticate other users and edit user privileges.