The Get-FileHash cmdlet of PowerShell allows you to create a checksum for files and these checksums uniquely identify the files. There are several algorithms that are practiced on a file to create a checksum. In this informative post, we will provide brief content on creating a PowerShell checksum using the Get-FileHash cmdlet.
How the Get-FileHash cmdlet works
The working of the Get-FileHash cmdlet depends on the syntax provided below:
The -Path parameter accepts the path of the file for which you are creating a checksum block.
By default, the Get-FileHash cmdlet creates a checksum using the SHA256 algorithm. However, the following algorithms can also be used in the -Algorithm parameter:
SHA2: Safer than SHA1 and widely accepted. The SHA-2 family comprises SHA512, SHA256, SHA224, SHA384. The most used among these are SHA512 and SHA256 because the other two are truncated versions of SHA256 and SHA512.
SHA3: The more secure and safe version than SHA2. Recommended for larger companies that require some extra security of their data transmission.
MD5: It worked well but several security breaches in the presence of MD5 made it a compromised one.
RIPEMD160: Introduced in the mid-1990s and several versions are available. Each newer version generates lengthy hashes therefore more secure.
Note: The above algorithms are supported by PowerShell 4 up till 5.1. However, PowerShell 6 and above versions only support MD5, SHA3, and all instances of SHA2.
How to create PowerShell checksum using Get-FileHash
This section practices several examples that are used to create checksum with Get-FileHash.
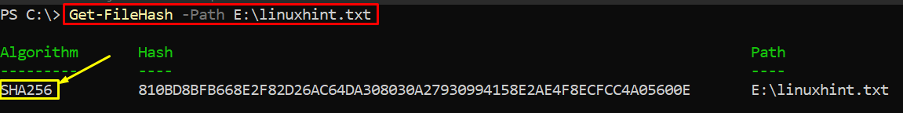
Example 1: Creating a checksum with default parameters
The command written below creates a checksum value for the file linuxhint.txt file. The output shows the name of the algorithm used to encrypt the file, the hash key, and the path of the file:
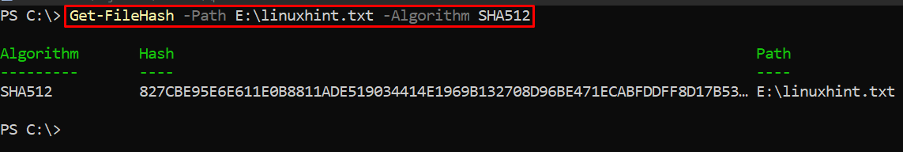
Example 2: Checksum using the user-defined parameters
The Get-FileHash cmdlet allows you to use hashing algorithm(supported) to generate a checksum file. In the below-stated command, we have generated hash using the SHA512 algorithm.
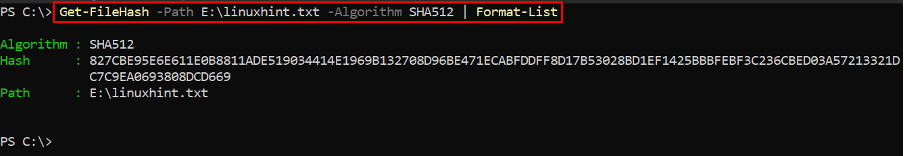
The above command can be formatted to get a clearer output as the hash of the file cannot be seen completely.
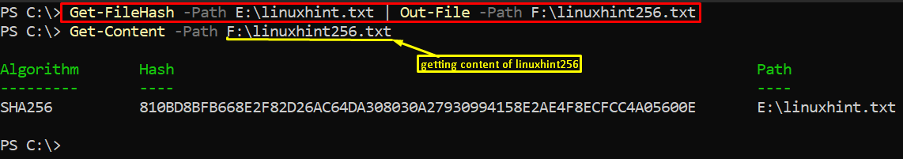
Example 3: Save the generated checksum in a file
The generated checksum must be saved for future use. So, here we have provided the command to save the generated output in a text file. The command written below generates the checksum and saves it in a file “F:\linuxhint256.txt“. And the Get-Content command is executed to check that the checksum has been stored or not:
> Get-Content -Path F:\linuxhint256.txt
Conclusion
The checksum is a validation agent widely used for validating the integrity of a file. The checksums are generated for a file being sent to the network/users. These checksums are compared at the receiver’s end to validate the content. This article practices the use of the Get-FileHash cmdlet to generate a checksum of a file. The Get-FileHash allows you to create checksums by supporting multiple hashing algorithms. You can either go for the default hashing algorithm or you can change it in the Get-FileHash cmdlet.