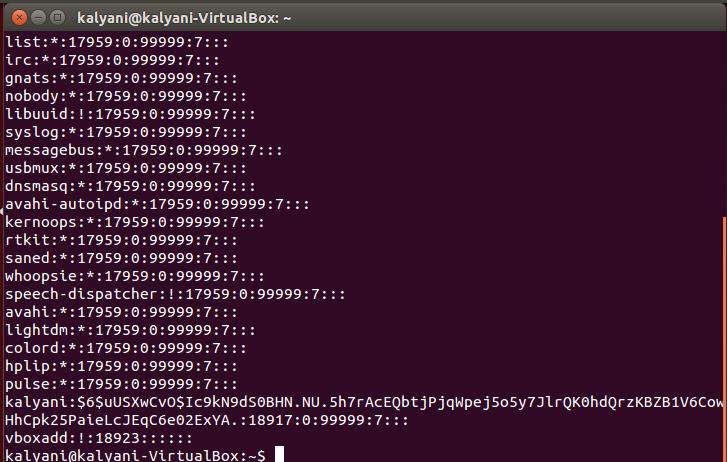
The shadow file contains information separated by a colon. So, it’d look something like this:
In my case, I’m going to pick out one of the users (user=kalyani) to use as an example.
B1V6CowHhCpk25PaieLcJEqC6e02ExYA.:18917:0:99999:7:::
Here, there are nine fields separated by colons!
1. The first field is the username itself. In my case, it’s kalyani, however, in your case, it’d be your username.
2. The second field contains the encrypted password
($6$uUSXwCvO$Ic9kN9dS0BHN.NU.5h7rAcEQbtjPjqWpej5o5y7JlrQK0hdQrzKBZB1V6CowHhCpk25PaieLcJEqC6e02ExYA.). Here, there are three-dollar signs. Between the first- and second-dollar sign is the type of encryption; between the second- and third-dollar sign is the salt, and after the third dollar sign is the hash itself.
Here, you can see $6$, what this means is that the encryption type is SHA-512. It’s as follows:
- $1$ – MD5
- $2$ – Blowfish
- $3$ – Blowfish
- $5$ – SHA-256
- $6$ – SHA-512
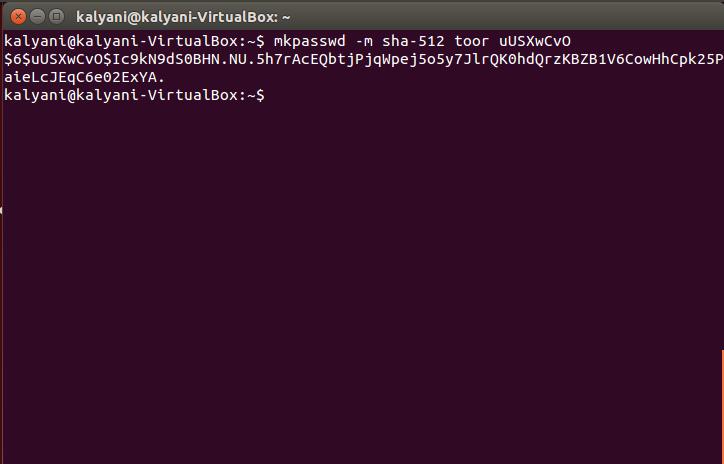
After that is uUSXwCvO, the salt. In order to make the hash more unique, we add what is known as a salt. The salt itself is a random sequence of characters. This random sequence of character is attached to the password while the hash is being computed.
If you want to try to check it yourself you can do so with the whois package. First, install the whois package:
Then, once the whois package has been installed, you can type the following:
In the latter, replace PASSWORD with the password you want and SALT with the salt you want.
For example:
The last part of the encrypted password or the stuff after the third dollar sign is the actual hash.
3. The third field is the date of the last password change. The number is calculated based on epoch (Jan 1st, 1970). What this means is that the number is calculated based on the epoch date. In my case, this number is 18917. If this field is empty, it means that the password aging features are not enabled. A 0 in this field means that the user must change his/her password on the next login.
4. The fourth field is the minimum password age. The minimum password age is the time in days that has to pass before the user can be permitted to make changes to the password again. A value of 0 means that there is no minimum password age. In my case, it’s 0. What this means is that on my system, there is no minimum password age.
5. The fifth field is the maximum password age. The maximum password age is the time in days it takes before the user is required to change the password. An empty value in this field means that there is no maximum password age. In my case, this number is 99999.
6. The sixth field is the password warning period. The user will be warned for a few days before the password will expire, this is the password warning period. In my case it’s 7.
7. The seventh field is the password inactivity period. The password inactivity period is the time in days when an expired password is still accepted. Once this period is over and that the password expires, logging in would be impossible. In my case, the field is empty, and what that means is that there is no password inactivity period.
8. The eighth field is the account expiration date. The account expiration date is exactly as it sounds, the day when the account expires. This number is expressed since epoch (Jan 1st, 1970).
9. The ninth field is a reserved field. This field is reserved for the future, and is currently not in use.
Changing the Password
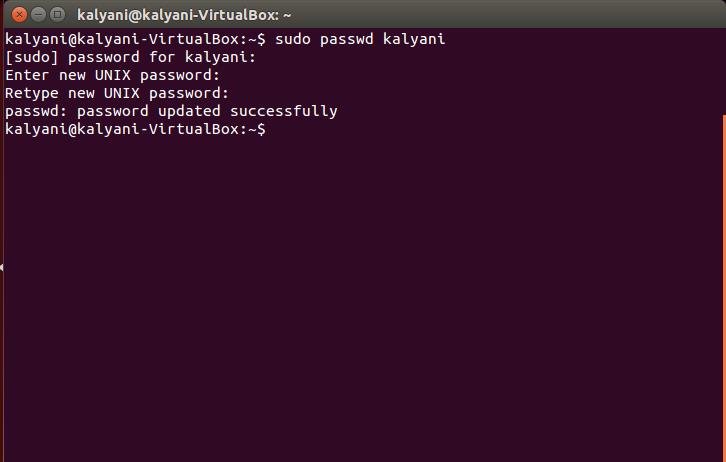
What all this means is that the password must be regularly updated or changed. The next question is how do we change the current password, and avoid all sorts of password aging problems? In order to change the password, one must be root!
Instead of {USERNAME}, enter your own username for which you want to change the password. It will prompt you for the current password. Once you enter it, it will ask you for the new password, and you can enter that too. And that’s it!
Change the User Password Expiration Information
Another piece of information that one might consider changing is the password expiration information. In such cases, the chage command comes in very handy!
For chage, you can use it with the following:
chage [options]
-d, –lastday
This is the date of last password change since epoch. It is written as YYYY-MM-DD.
-E, –expiredate
This sets the date on which the account will be disabled. The date itself is expressed as YYYY-MM-DD, and is since epoch. If you pass -1, there will be no account expiration date.
-h, –help
This will display help.
-I, –inactive
This sets the password inactivity period. If you put -1 in the inactive field, then there will be no inactivity information.
-l, –list
This displays password aging info.
-m, –mindays
This sets the number of days between password change. If you put 0, it means that the user can change his/her password at any time.
-M, –maxdays
This sets the maximum number of days when the current password is active. If -1 is passed, it will remove the checking of the validity of the password.
-W, –warndays
This sets the password warning period.
The shadow file is by far the most important file on your Linux system. Previously, the passwd file used to contain all the passwords, but these days, the passwd file is a plain text file that contains user information, and the shadow file instead contains all password information! And because it contains password information, it is both locked to the super user, and hashed (encrypted).
Within the shadow file are one-liners containing nine fields separated by colons, each of which expresses a password information or a password aging information. Either way, the shadow file is one to be both protected, and locked!
Happy Coding