As an ethical hacker, you will use the “Kali Distribution,” which includes the community edition of Metasploit and additional ethical hacking tools. However, if you wish to install Metasploit only as a distinct tool, you may do so simply on Linux, Windows, or Mac OS X platforms. We are using kali Linux in our tutorial.
Accessing Msfconsole
MSFconsole is a command-line interface for working with and accessing the Metasploit Framework. The MSFconsole is perhaps the most frequently used Metasploit Framework user interface. Scanning targets, exploiting vulnerabilities, and collecting data are all possible by using the console. You can access msfconsole by the execution of the following listed command.
Now we are going to load the msfcrawler by using the following affixed command.
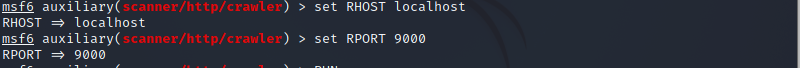
There will be no specific out for the above-listed command. Now you must check for RHOST that is a URL or IP address, such as localhost and RPORT, which is a port number you have to join. In our case, we have used port number 9000.
> set RPORT 9000
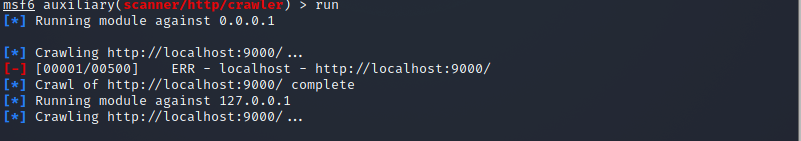
The output depicts the clear picture that both RHOST and the port number have been adjusted accordingly. Now the time comes that we have to run the relevant crawler. Utilize the below-appended instruction for this purpose.
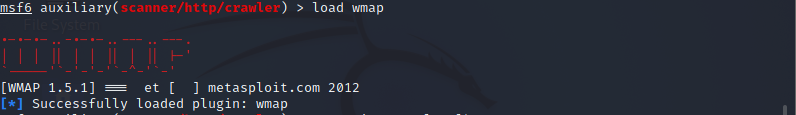
After getting done with crawling, the load wmap command makes loading the WMAP module straightforward, as shown in the affixed screenshot.
Now you have to use the -a flag preceded by the site address using wmap sites to add a site.
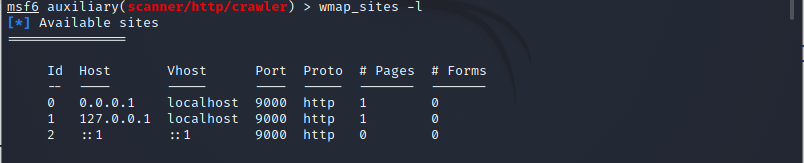
Using the -l parameter on wmap sites, we could now list the accessible sites. To execute the appended below command to get your work done:
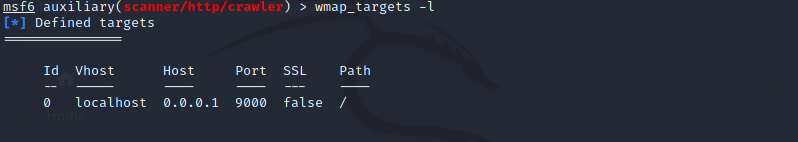
Now we must include this website in our targets by the execution of appended below command.
“0” reflects the id of the attached site mentioned in the above instruction. Next, we will use wmap targets to specify the precise target URL we want to scan. To display the defined targets, execute wmap targets with the -l argument.
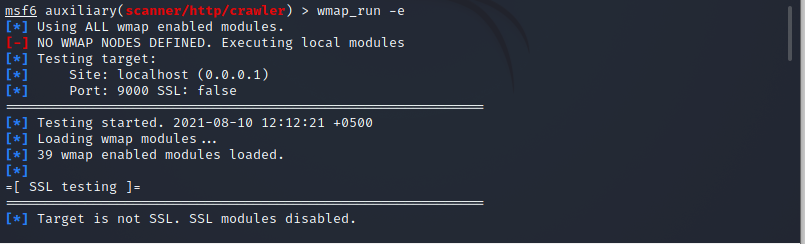
Let’s start running the wmap run with the -e flag, which will execute all of the modules rather than just one. The scanning can take a long time to complete depending on the target site and the number of enabled modules. The scan will indicate how long it would take to complete after it’s finished. To execute the cited below instruction in the terminal.
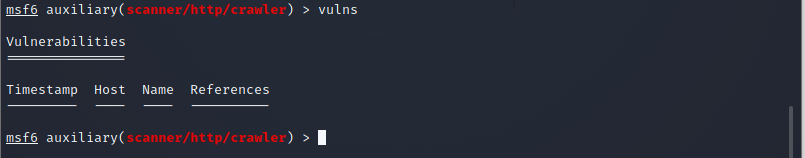
There are components for directories testing, query testing, web application testing, and SSL testing; however, as our target does not use SSL, these modules are deactivated. After the scanning is complete, we may view the vulnerabilities that have been identified with the help of the listed command.
WMAP might not produce as extensive data as other web vulnerability scanners, but this insight might be a valuable jumping-off point to explore different lines of attack. This scanner can be quickly loaded and utilized from inside the Metasploit Framework, which makes it a handy tool to learn how to use.
Conclusion
The Metasploit Framework is a collection of tools for testing security vulnerabilities, enumerating networks, executing attacks, and avoiding detection. We learned how to use the WMAP plugins to analyze a web application for vulnerabilities. I hope now you will get a lot of knowledge regarding vulnerability scanning using the Metasploit framework in Kali Linux.