SSH is a secure way of connecting to a remote server. With SSH, the client machine must get verified before it connects to the server, and that is done using a password and an authentication key, which can be public or private.
The authentication keys ensure that you safely connect to your server using the OpenSSH for Linux. This guide details how to use a private SSH key for authentication. We will discuss everything from generating the SSH key to using it when connecting to the server.
Generating the Private SSH Key
To generate the private keys, we need to run the ssh-keygen command which will guide you in generating the private key and the involved details, such as the filename and the passphrase. When the private key is generated, it is best to store it securely.
Let’s create a hidden folder on the server that stores the generated key once we generate it on the client machine and copy it to the server. We can name the hidden folder as ssh.
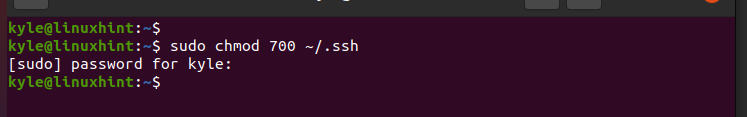
Note that we create the hidden folder on the server, not on the client. Next, change the directory permissions so only the owner can interact with it. This way, you keep your private key secure.
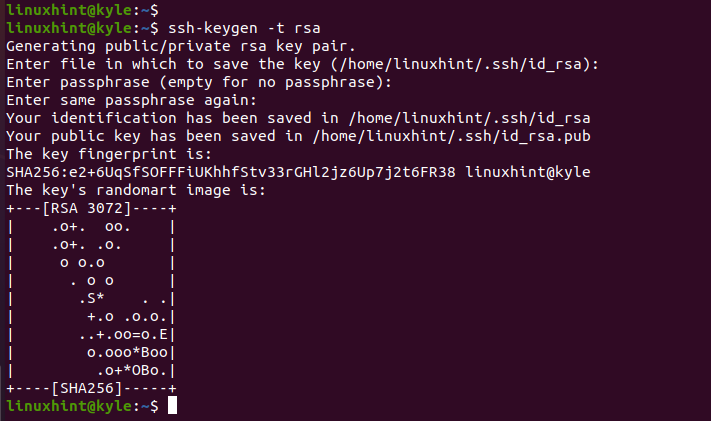
With the created secure folder in your home directory, you can generate the private SSH key on your client machine. Make sure that you have the OpenSSH installed. Then, execute the following command to create your new key pair:
You will get prompted to provide different details, including the name of the private key and the location where you want to save it. You can use the default options by pressing the enter key. You can optionally add a passphrase to enhance authentication.
Copy the Generated Private SSH Key to Your Remote Server
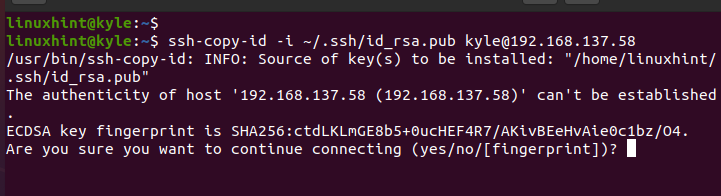
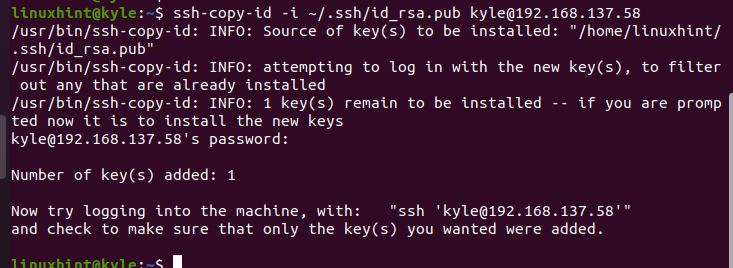
The generated private key must be copied to the client, such that when connecting via SSH, the connection gets established by checking the private key to authenticate the client. Use the following syntax and replace the details to match your username of the server and its IP address. Also, if you changed the name for the private key, replace it and its path.
Note that we specify the path that we created earlier for our hidden folder because that’s where we want to store the private key. The id_rsa.pub represents the default naming of private SSH keys.
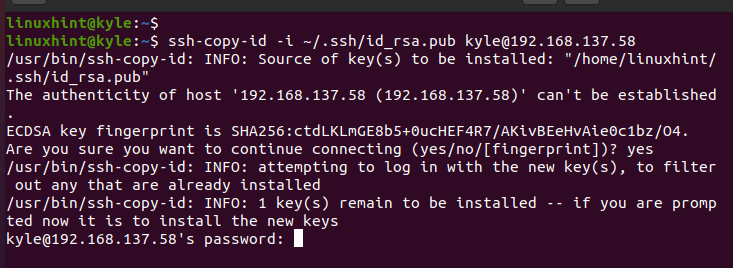
Press yes to continue with the SSH connection. Then, enter the password for the server that you are connecting to.
You will get a message which confirms that the private key is copied to the target server and that you can now SSH to the remote machine to verify that your private SSH key is added successfully.
How to Use SSH Using Private Key
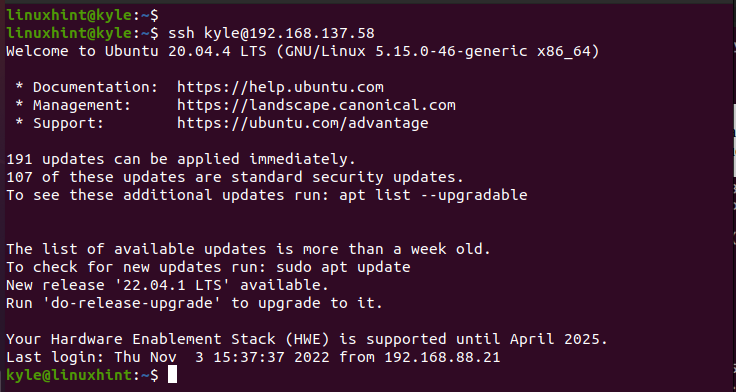
So far, we generated the SSH private key and copied it to the remote server. Now, let’s login the SSH to the remote server to verify that we can use the SSH using the private key.
If the private key is copied successfully, we should be able to log in to the remote server without any further verification, as in the following output:
We managed to login the SSH using a private key in Linux.
Conclusion
SSH is the secure option for logging in to a remote server. When using SSH, you can generate the private keys and copy the file to the remote server, such that when you want to SSH, you can authenticate the session using the private keys. This guide has detailed everything about using SSH private keys, from generating the private key, to copying them to the target server, to logging in using the private key.