To successfully solve this problem, we must determine the root cause of this error. This article will provide you the most likely reasons and offers their effective solutions in detail. Follow the article to learn the methods for fixing this error.
“Connection reset by peer” ssh error causes
This ssh identification error claims that the TCP stream was suddenly closed by the remote machine. Sometimes, a remote server reboot can quickly resolve a brief outage or the connectivity issue.
You can prevent error occurrences in the future on your system by learning how to diagnose this issue and discovering its underlying cause. We have compiled the common reasons for you to identify the leading cause of this connection reset by peer error.
- The SSH daemon file related to the configuration has been modified.
- By upgrading firewall rules, intrusion prevention software blocked your IP address.
- Due to Host-Based Access Control Lists, the connection is being banned.
Method 1: Checking host deny and host allow files
Editing host.deny file
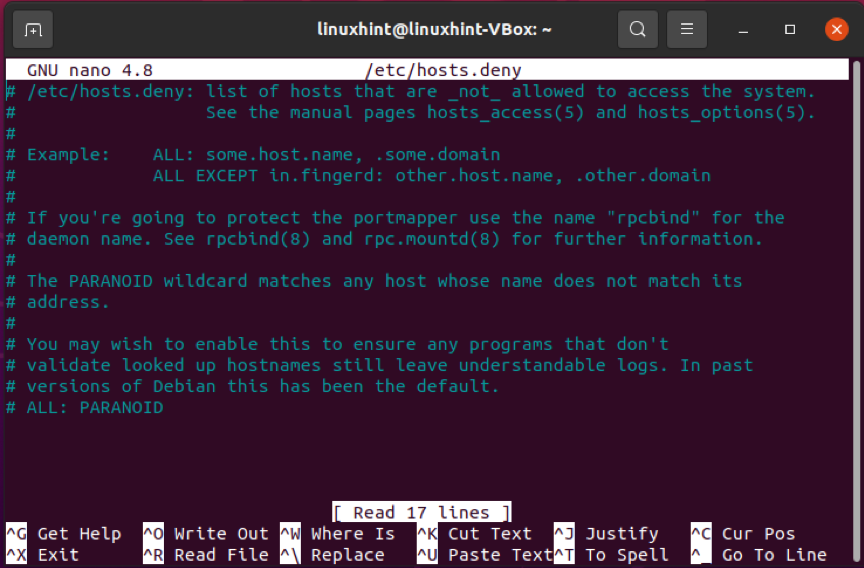
TCP wrappers are the hosts.deny and hosts.allow files. These files are utilized as a security function for limiting the hostnames or IP addresses connected to the remote system. Using your favorite text editor, connect to your remote server and open up the hosts.deny file. Write out the below-given command if you are using nano on a Linux-based system.
Comments are lines that are left blank or begin with the ‘#‘ symbol. Verify that this host.deny file contains your local IP or hostname. If you found out, immediately remove it or comment it out because it will not connect remotely.
Save the host.deny file and exit after making the necessary modifications. After this, make a retry to connect through SSH.
Editing host.allow file
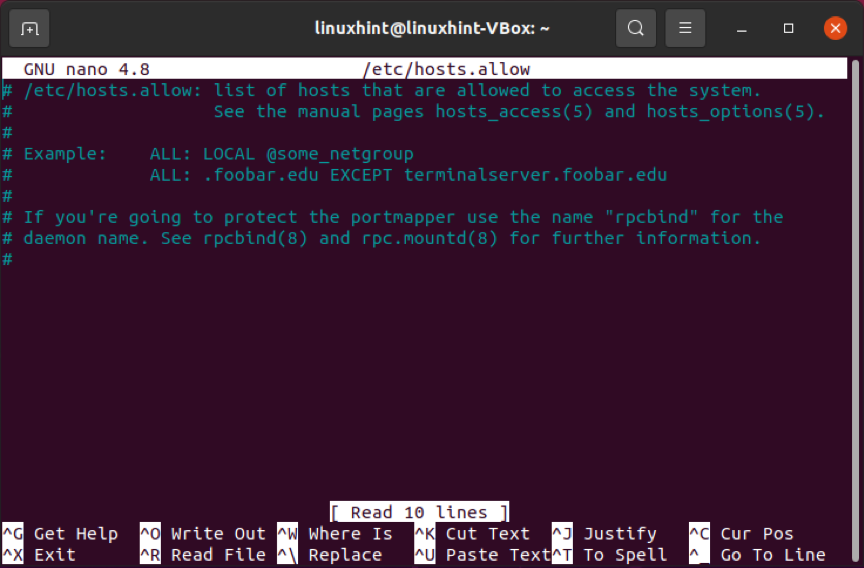
Edit the hosts.allow file as an extra precautionary measure. Within the hosts. In this file, the existed access rules will be first applied. This file takes superiority over the host.deny the file. To view the hosts.allow file, execute the below-given command:
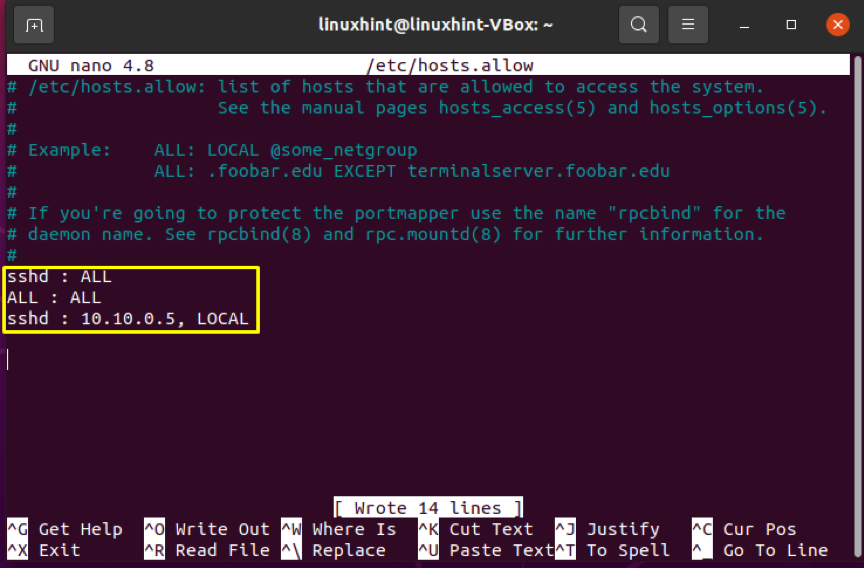
Adding IP addresses and hostnames to the host.allow file creates exceptions for the hosts.deny file settings. For example, creating a policy in host.deny file for restricting access to all hosts. After this, you can edit the hosts.allow the file to add any single IP range, IP address, or hostname. Only the specified IP will be allowed to make an SSH connection with your remote server after writing out these lines in your host.allow file:
ALL : ALL
sshd : 10.10.0.5, LOCAL
Remember that a security setting like this will restrict your ability to control and maintain your remote servers.
Method 2: Checking the sshd_config file
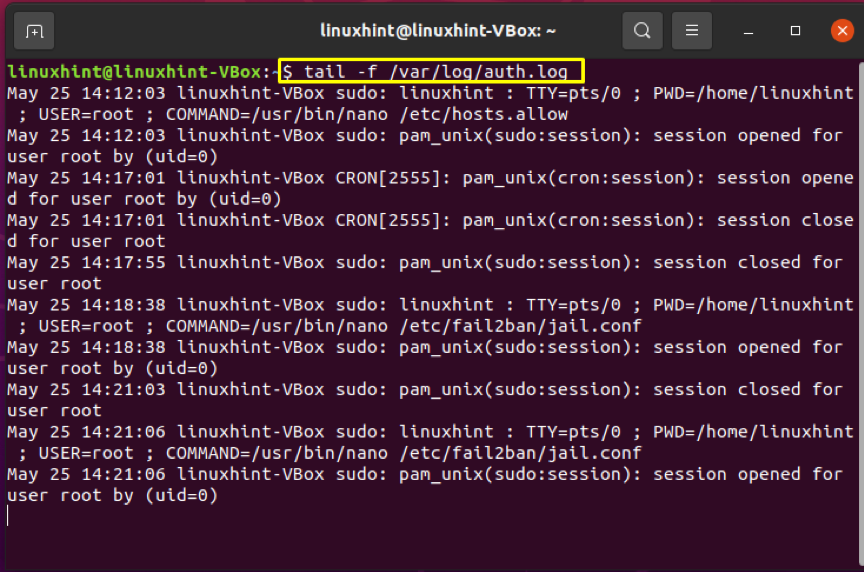
Investigate the authentication log entry if you are still getting the subject error. The SSH daemon transmits information related to logging to the system logs by default. After you are failed to log in, check out the /var/log/auth.log file. To look at the most recent log entries, write out this command:
The execution of this command outputs information related to your user account, its password, authentication key, as well as the outcome of your authentication attempts.
The log contains information that will assist you in locating potential errors in the sshd configuration file. For example, when an ssh connection is established, the modifications made to the log file will modify the agreed terms, which also causes the remote server to reject the client. Type: sshd config to open up to the sshd config file.
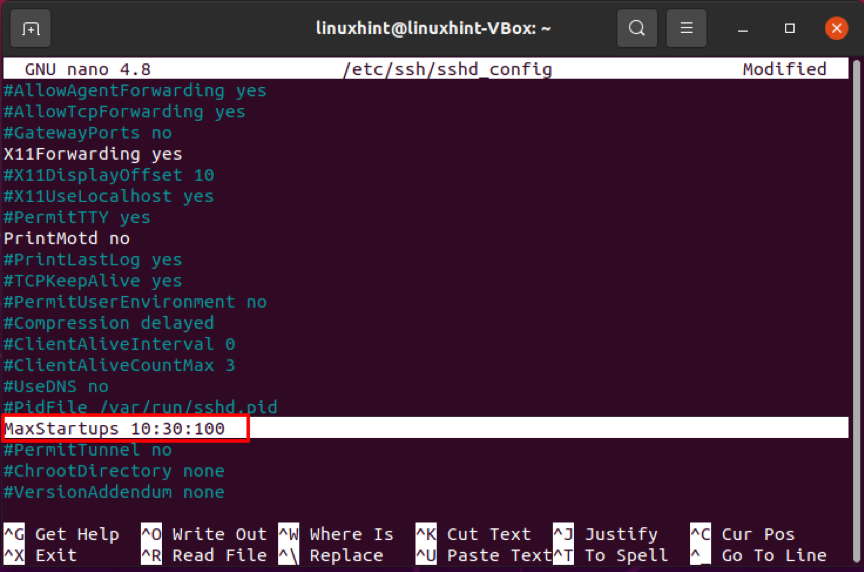
Primary settings, such as the authentication of the ssh key pairs, TCP port, can be changed in the sshd configuration file and the other complex capabilities like forwarding port.
If you make changes to the sshd config file, you must restart the sshd service for them to take effect.
Conclusion
The number of possible causes is enormous, and troubleshooting them is challenging in every way. If the ssh exchange identification error persists, your host may need to be contacted. In this article, you have gone through the most common causes of the “ssh exchange identification: read Connection reset by peer” error. Now, you should successfully solve the problem and know how to cope with similar challenges in the future by looking at each possibility one at a time.